There are essentially three threat paths that bad actors take to access an Active Directory in order to compromise and control a hospital system: social engineering, third-party compromise, and system vulnerability compromise. In our new webinar, Intermountain Health’s cybersecurity director, Shawn Anderson, explores proven ways to strengthen Active Directory security by thwarting intruders’ attempts to escalate privileges and achieve total domain dominance.
Fresh Insights on Active Directory Security
If an attacker gains access to a domain admin in your Active Directory, it’s game over. You’ve lost control of your environment – and that’s how health systems get taken offline. When that happens, patient health is in jeopardy. The best way to disrupt the attacker’s playbook is to make sure that the privilege escalation path is broken.
The diagram below shows the three tiers of a typical healthcare system. Attackers will initially try to penetrate the ordinary workstations and devices in Tier 2. If intruders succeed in harvesting credentials in that tier, they’ll move quickly into Tier 0 (Active Directory databases and domain controllers). Then it’s Pearl Harbor time: dropping Cobalt Strike and launching ransomware that hits all three tiers.
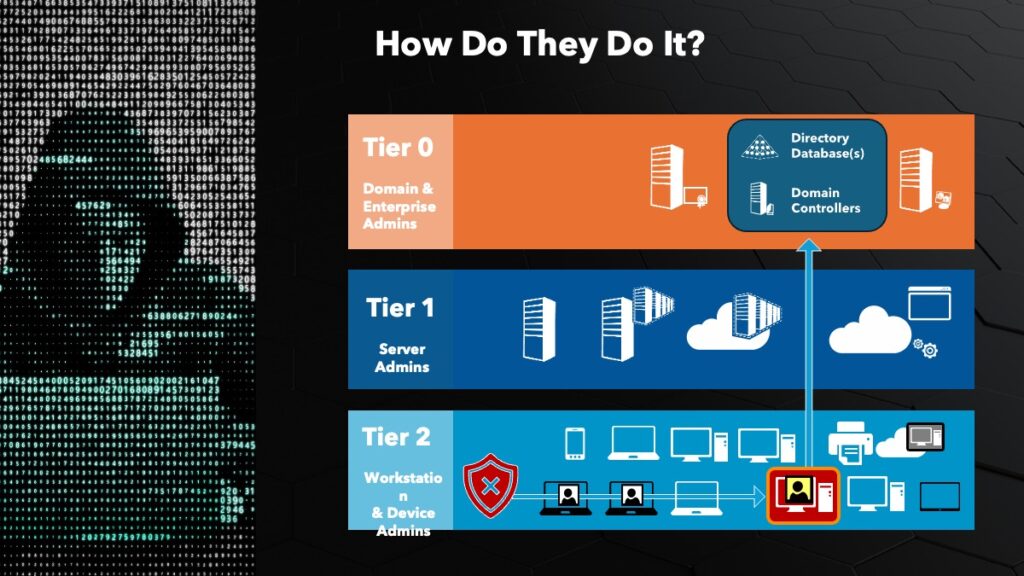
If attackers gain control at the top, they’ll continue to compromise the tiers below. That’s what leads to really long outages at hospitals because they have to rebuild everything from scratch. It’s a very time-consuming – and extraordinarily expensive – process.
Historical Perspective On Active Directory Security
Most cybersecurity professionals learned about the Bell-LaPadula model in their college studies. Developed by David Elliott Bell and Leonard LaPadula for the U.S. Department of Defense in 1973, it remains highly relevant today.
The Bell-LaPadula model emphasizes “no control up, no exposure down.” If you’re in Tier 2, you cannot take control of anything in the tier above you. No exposure down” means that no credentials or authentications on a higher tier can be compromised and used maliciously in Tier 2.
Keys To Preventing Privilege Escalation
Using the Bell-LaPadula principles to strengthen Active Directory security involves five deployment measures:
- Analyze and review Active Directory security
- Reduce excessive admin privileges
- Segment credentials into privilege tiers
- Block access between tiers
- Use a privileged access workstation for administration tasks
The Importance of PAWs
A privileged access workstation (PAW) is a dedicated admin workstation per tier, per administrator – and access is blocked between tiers.
It’s important to note that a PAW is not a jump server. It’s not a resource in Tier 1 that you can access from Tier 2. A jump server that crosses tiers violates the “no control up” principle. So, if you administer things in more than one tier, you need a PAW for each tier.
It’s also worth noting that a PAW is a protected physical keyboard. You need to make sure that the connection from the keyboard to the domain controller is clean and has the expected security profile. Using a virtual PAW violates the “no control up” principle.
Finally, PAWs should contain no productivity software – no Microsoft Teams, no Outlook, no Google Drive, etc.
Enhancing Active Directory Security: The Pushback
If you try to bolster Active Directory security using PAWs, you’ll probably hear some grumbling from hospital IT staff. Common complaints include “this is going to decrease productivity” and “PAWs will make our admins mad.” When you watch the webinar, you’ll get tips on how to counter those objections.
Enhancing Active Directory security isn’t a simple task, but the webinar will answer many of your questions as it provides a detailed action plan for implementation.
It may seem like a real pain to monitor PAWs around the clock and perform the continuous patching needed to ensure every admin has a unique PAW and knows how to manage it. But those headaches pale in comparison to the financial and human cost of having your hospital go offline for an extended period.
Click here to view our informative webinar on “Active Directory Isolation: Disrupting The Bad Actors’ Playbook.”