Our service delivery model is expertly designed to navigate the ever-changing threat landscape. Clients choose us for our specialized healthcare focus and unparalleled range of Advisory and Threat Defense services. They stay for our partnership approach, tailored to their unique healthcare challenges.
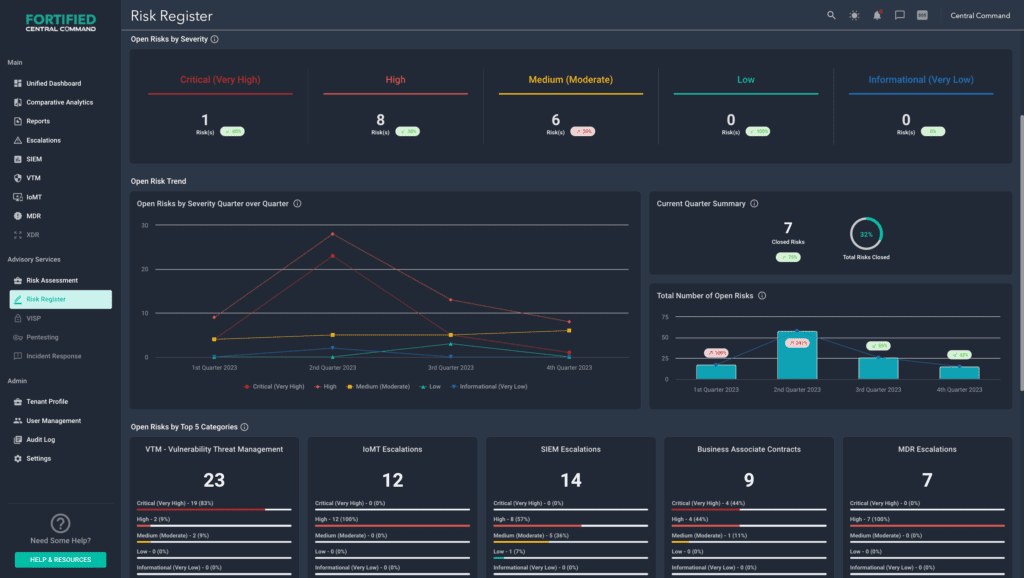
Detecting and remediating threats is just the beginning. To effectively safeguard patients, data, and IT infrastructure, you need rapid, actionable insights.
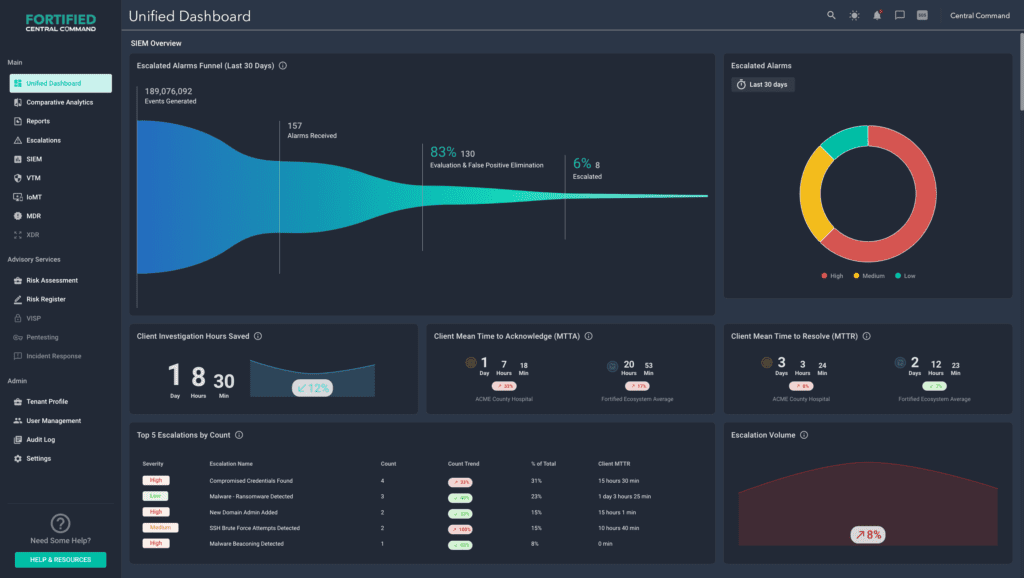
Fortified’s 24/7 Threat Defense center and dedicated security analysts provide vigilance and context-rich escalations consistently rated at 95% valuable.
“There are many cybersecurity providers that understand the technical aspects of what needs to be done and why. But if they haven’t applied that knowledge within a healthcare organization, they just don’t get it. And that makes it difficult to make real progress. With Fortified, I don’t have to sit there and explain repeatedly why I can’t do something or why we can’t patch a certain vulnerability related to a medical device. They already know the answer. In fact, many times they guide me on what we should do so that we don’t inadvertently break something critical to serving patients. Having a partner with that experience and expertise is priceless.”
– Health System ISO

"Having a partner with that experience and expertise is priceless.”
We meet you where you are.
With our nationwide presence and end-to-end portfolio of healthcare cybersecurity solutions, we meet you where you are in your cybersecurity journey, and take you where you want to go.
Resources
© Copyright 2024 Fortified Health Security, Inc. All rights reserved. Contact Us | Terms of Service | Privacy Policy | Cookie Policy