Since the start of 2025, the healthcare sector has continued to experience cyber incidents that have disrupted patient care, exposed millions of records, and reshaped organizational thinking about resilience. Cybersecurity Awareness Month is not just about reminding people of risks; it’s about translating real-world events into actionable lessons.
Below is a look back at the most impactful incidents of 2025 so far, along with the lessons healthcare leaders can carry forward.
1. Third-Party Risk at Scale
Case: Change Healthcare, 192M individuals affected
What happened:
The 2024 breach at Change Healthcare’s (UHG tech unit) number of affected people was updated in July 2025. A data review revealed it affected 192.7 million people, nearly doubling earlier estimates. The compromise involved third-party vendor systems exposed through weak remote access controls (lack of MFA on Citrix service), with exfiltration and disruption of claims processing. The final estimated number makes it the largest healthcare-related breach in U.S. history. This event served as a wake-up call about the vulnerability of critical third parties that sit at the heart of healthcare operations.
Lesson learned:
This incident highlights the risk of concentration. A single vendor with foundational roles (e.g., claims processing) can create systemic exposure through a single point of failure.
For CISOs, this means:
- Inventory and classify third parties based on operational criticality.
- Demand strong controls in contracts—MFA, encryption in transit and at rest, and annual penetration testing.
- Extend tabletop exercises to vendors, ensuring they know their role in your downtime procedures.
2. Emergency Department Diversions
Cases: Kettering Health (Ohio, May) | St. Mary’s & Central Maine (Lewiston, June)
What happened:
Both a large Ohio health system and two regional hospitals in Maine were forced into diversion after ransomware attacks disabled their systems. At Kettering, Epic access created downtime that stretched across multiple weeks. In Lewiston, two different hospitals went down within weeks of each other, straining regional emergency services for all local communities.
Lesson learned:
Ransomware is now a patient-safety event, not just an IT incident. Treatment of ED diversion should be as a measurable cyber impact. Hospitals need:
- Practiced diversion protocols with local EMS and regional health partners.
- Downtime playbooks that assume paper operations for 48–72 hours.
- Reconciliation workflows for safely re-entering clinical data back into EHRs after downtime.
3. Clinic & Physician Network Exposure
Case: Frederick Health Medical Group (Maryland, January – ~934k affected)
What happened:
Ransomware impacted Frederick Health’s clinic network, resulting in temporary diversions. The attack highlighted vulnerabilities in sprawling physician networks, where thousands of endpoints connect back into a central system.
Lesson learned:
The attack showed the danger of treating outpatient clinics as “lower risk.” Segmentation is critical:
- Isolate clinic systems from hospital core networks to reduce impact.
- Ensure independent access controls for outpatient facilities.
- Train staff at smaller sites on emergency procedures, since attackers often target the “weakest link.”
4. Rural Healthcare Under Siege
Case: Aspire Rural Health System (Michigan, accessed Nov 2024–Jan 2025, disclosed August)
What happened:
Attackers quietly maintained access for months before exfiltrating data from Aspire Rural Health, impacting 138k patients. The delayed discovery reflected a lack of continuous monitoring and the resource challenges that rural hospitals face.
Lesson learned:
Smaller systems are also vulnerable; threat actors often view them as a softer target. What’s missing is 24/7 detection and response, providing that early visibility can lead to preemptive actions for containment. For rural providers:
- 24/7 Managed Endpoint and Network Detection and Response (Managed EDR/NDR) services can close the gap where staff coverage is limited.
- Cross-organizational collaboration (with regional health systems or MSSPs) can establish cross-organizational collaborations, providing access to expertise that would otherwise be unavailable within your own organization.
- Advocacy for rural cybersecurity funding should be a key part of the CISO’s voice at both the state and federal levels.
5. Dialysis & Specialty Providers
Case: DaVita (nationwide) ~ 2.7 million individuals impacted
What happened:
In April 2025, DaVita, the largest dialysis provider, discovered a ransomware attack that accessed its labs database. Despite continuing care, the breach exposed patient information (including clinical, insurance, and identity data). The company incurred approximately $13.5 million in remediation costs in Q2 2025, driven by this breach.
Lesson learned:
Specialty providers are high-value targets due to the critical services they provide and the often sensitive datasets they manage. Dialysis, oncology, and other high-dependency services cannot tolerate downtime. For these organizations, you should:
- Limit PHI replication across labs and contractors to minimize data available for exfiltration, leveraging strong segmentation of PHI data.
- Segment backups and store them immutably to ensure continuity and data integrity.
- Align disaster recovery with care-critical services, not just IT systems.
6. Extended Dwell Time & Delayed Detection
Cases: Central Maine Healthcare (unauthorized access Mar–Jun, disclosed July)
What happened:
Attackers maintained unauthorized access for over two months before it was detected. This kind of extended dwell time magnifies the potential for data theft and operational disruption.
Lesson learned:
Dwell time remains one of healthcare’s biggest blind spots. MTTD (mean time to detect) must be tracked and reduced. Deploy continuous monitoring solutions (EDR/XDR, SIEM, anomaly detection) and pre-authorize response capabilities, including cutting off access under suspicious activity.
Continuous monitoring, anomaly detection, and empowering staff to act quickly are essential.
- The measure of mean time to detect (MTTD) must be tracked and reduced.
- Pre-authorize response capabilities to disconnect systems or cut access during suspicious activity.
- Invest in continuous monitoring (EDR/XDR, SIEM, Anomaly Detection) to increase detection and limit attacker persistence.
7. Regulation & Policy Momentum
- HIPAA Security Rule (proposed update): Emphasizes encryption, MFA, incident response, business associate notification timeliness, within 24 hours.
- CIRCIA (final rule delayed to 2026): Organizations should build compliance capabilities now, and mandatory reporting requirements are coming (72-hour reporting of incidents and 24-hour reporting of ransomware payments).
- HHS Cybersecurity Performance Goals (CPGs): Continue to serve as the de facto minimum-security posture in healthcare.
Lesson learned:
Regulation convergence with cybersecurity best practices offers both risk obligations and opportunities for alignment. CISOs should:
- Map controls to CPGs now to demonstrate progress.
- Prepare reporting templates that anticipate CIRCIA requirements.
- Review vendor agreements to ensure compliance with shorter notification windows.
Top 10 Key Lessons to Carry Forward
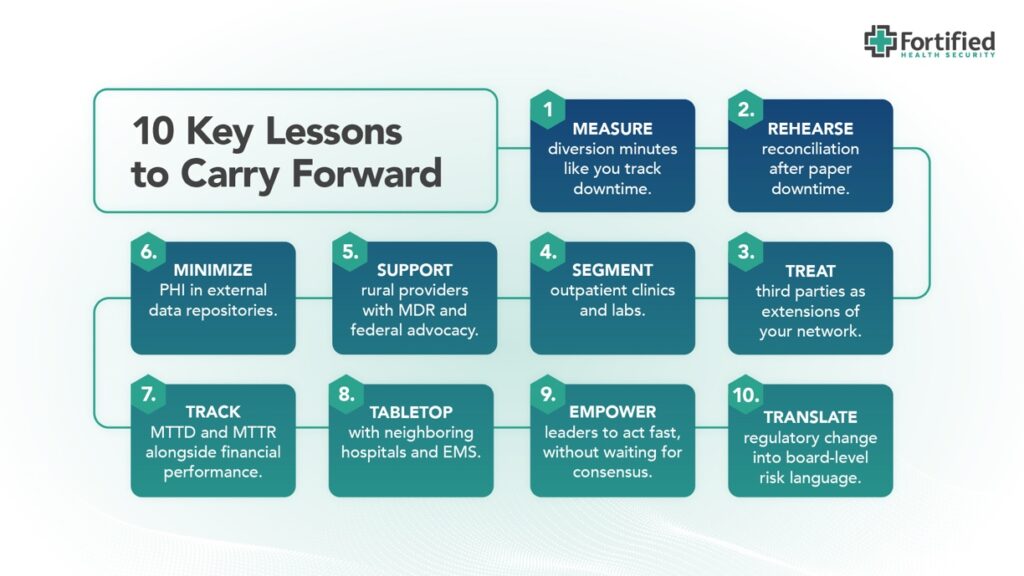
- Measure diversion and disruption of care in minutes like you track downtime.
- Practice paper-based operations and rehearse reconciliation workflows assuming 48-72 hours of system downtime.
- Treat third-party vendors (especially those with critical processing roles) as extensions of your risk surface; embed security in contracts and operations.
- Segment outpatient clinics, specialty labs, and home-based services from the core network.
- Leverage MDR / MSSPs to provide monitoring & response capability, particularly for rural/smaller providers with limited internal staffing.
- Minimize PHI exposure in external or third-party data repositories, limit data replication, and ensure encryption with immutable backups.
- Track MTTD and MTTR alongside financial and clinical performance metrics.
- Conduct joint tabletop exercises with neighboring hospitals, EMS, and vendors that include realistic cascading failure/diversion scenarios.
- Empower operational and executive leaders to act fast, without waiting for consensus.
- Translate regulatory change into board-level risk language, including likely liabilities, fines, and patient safety exposure.
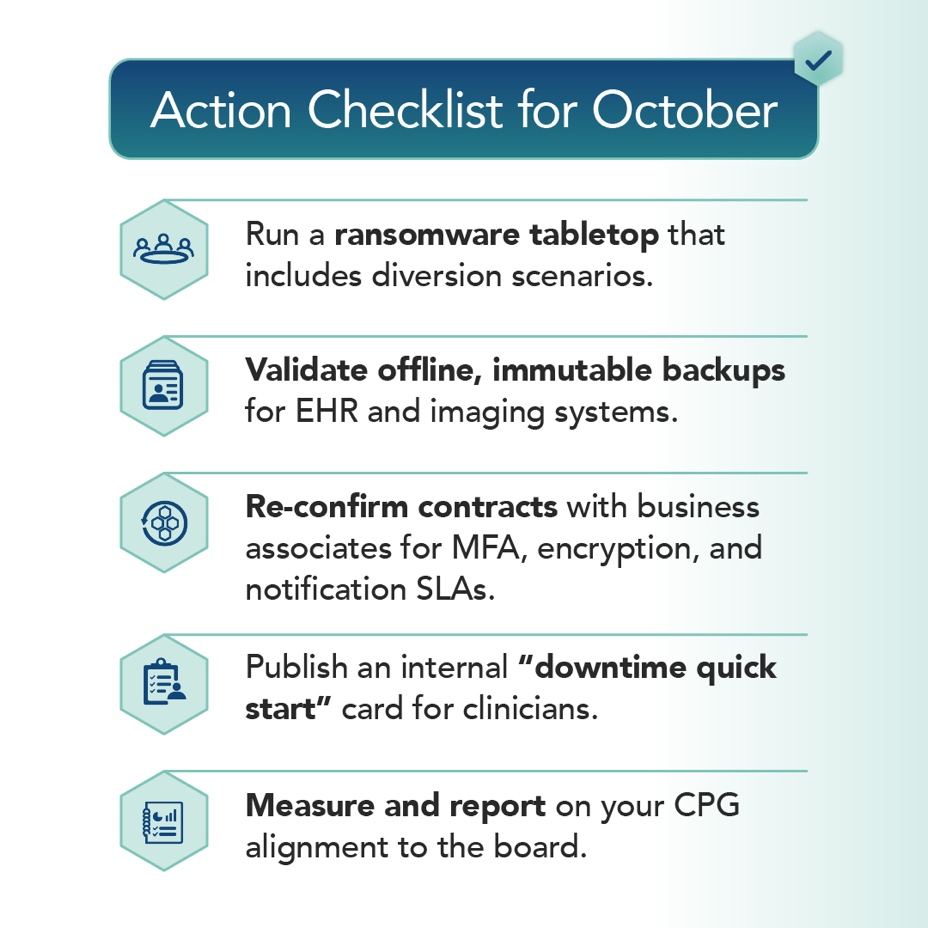
Action Checklist for October
Closing Thought
2025 has proven once again that cybersecurity is not just about protecting data; it’s about protecting patients and the resiliency of the patient care continuum. Every diversion, every delay, and every record exposed has real-world consequences.
This Cybersecurity Awareness Month, let’s commit to learning from these incidents, strengthening our programs, and defending differently so that care delivery remains uninterrupted. The time to act is now; stop waiting for mandates or regulations while leaving your organization exposed to known risks and vulnerabilities.
