Horizon Report
The state of cybersecurity in healthcare

As an industry, healthcare faces a significant uphill challenge when it comes to safeguarding sensitive patient data. Cybersecurity threats and malicious actors continue to focus on exploiting patients by compromising their personal health information and endangering their care by significantly disrupting hospital operations, as other countries experienced with WannaCry.
This single attack caused many healthcare IT organizations to spend the weekend — or weeks, in some cases — deploying a critical security patch that Microsoft issued on March 14th, almost two months prior to the attack. Organizations that were still running older, unsupported versions of Microsoft Windows were initially at risk until they released an emergency security patch for these older platforms as well.
Cybersecurity threats at their core are patient safety risks and, frankly, the stakes are too high. My hope is that the Horizon Report builds awareness about threats and provides you valuable insight. We welcome your feedback and perspectives at horizonreport@fortifiedhealthsecurity.com. Enjoy.
Regards,

Dan L. Dodson
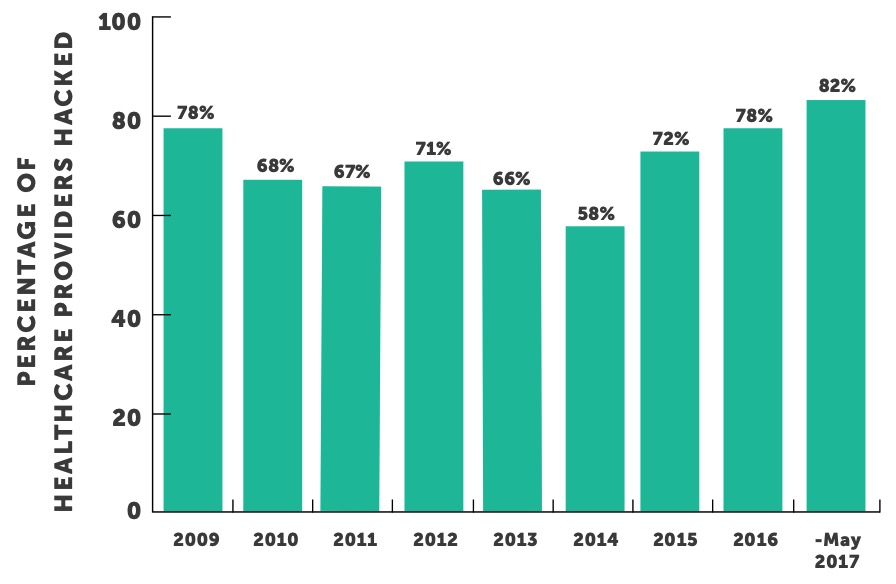
It took only three days for the first data breaches of a health plan in 2017 to be reported to The U.S. Department of Health and Human Services’ Office for Civil Rights (OCR). It was only five days until a healthcare provider first reported a breach of over 500 patient records, according to the OCR Wall of Shame. This just so happens to be one day faster than in 2016, but this sends the same chilling message: there is still a ton of work to be done to better protect personal health information.
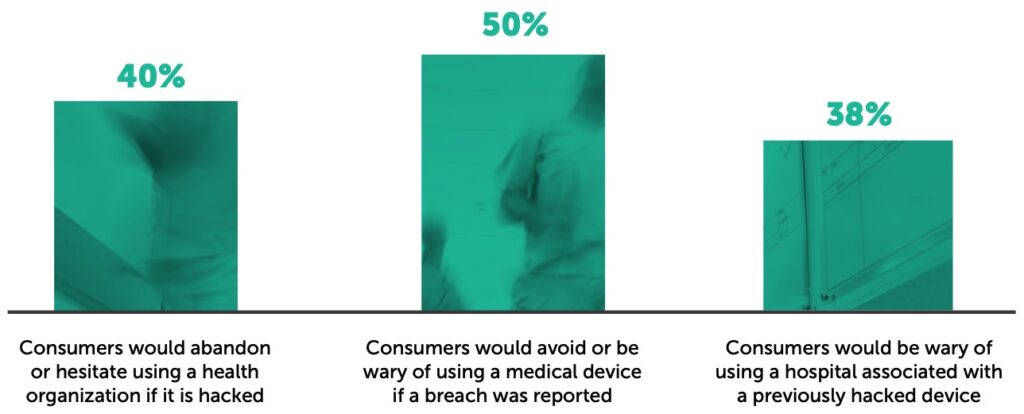
These breaches are coming at a time when patients are starting to act more like consumers. This forces healthcare organizations to guard their reputations, develop strategies for better patient engagement, and provide increased amounts of sensitive data to multiple interconnected devices. Recognizing the potential impacts of a breach on an organization before one occurs is important as many health systems only start investing in cybersecurity after they have been negatively impacted by an incident and, at that point, it may be too late for some patients. Reports* suggest that nearly forty- percent of consumers would abandon or hesitate using a health organization if it is hacked. Fifty- percent of consumers would avoid or be wary of using a medical device if a breach was reported and thrity-eight percent would be wary of using a hospital associated with a previously hacked device.
If breached, a healthcare organization’s patient engagement initiatives and perhaps their revenue (if it causes a decrease in patient volume) may be significantly impacted due to public perception. However, the potential impact of a breach could be even greater for medical devices due to their direct interaction with patients. While no hacked medical device is known to have caused patient harm to date, the ramifications to the healthcare industry due to this type of breach could be catastrophic. The good news is that some healthcare organizations are starting to recognize the potential risks associated with medical devices and are prioritizing their security.
According to one poll, twenty-three percent of healthcare organizations stated that lax security on devices is their biggest concern which ranked second only to mobile device hacking which twenty-nine percent cited as their highest priority for 2017. Overall, fifty-eight percent of healthcare organizations ranked Internet of Things (IoT) device security, which includes connected medical devices, a high priority for 2017.*
Regardless of the attack vector, an organization that experiences a significant reportable breach could be in for a big drop in patient confidence. Unfortunately, the number of healthcare entities that reported a significant data breach over the past twelve months has increased almost nineteen percent over the prior twelve-month period. The increase in entities impacted by a breach was largely driven by the healthcare provider segment as they experienced over thirty percent increase during those periods. Healthcare providers continue to be the biggest target and experience more breaches than health plans and business associates combined.
Ransomware is malicious software which blocks access to computer systems and data on network shares until a sum of money is paid. WannaCry is a brand new type of ransomware that is being deployed through remote exploits. WannaCry ransomware infections stopped operations for dozens of hospitals in the UK. The cyber attack has hit more than 300,000 computers across 150 countries since the initial release. The attack vector anatomy was comprised of the following factors:
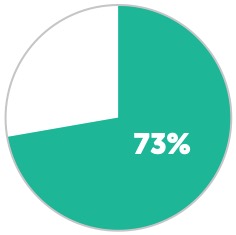
Percentage of healthcare organizations that have a business continuity plan in place in case of a ransomware attack.
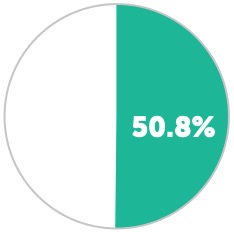
Percentage of providers who say they would not pay a ransom to get a patient’s data back.
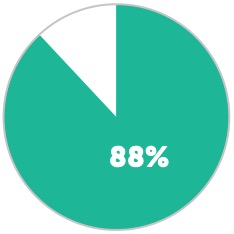
Percentage of all ransomware attacks on U.S. companies in 2016 that were tied to the healthcare industry.
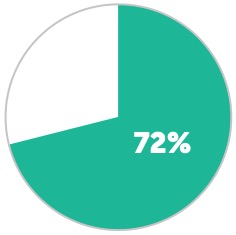
Percentage of infected business users who could not access their data for at least two days following a ransomware attack.
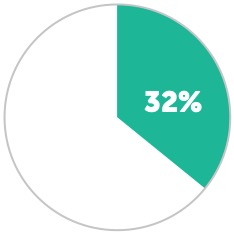
Percentage that lost access for five days or more.
*Source: (Modern Healthcare, 6/20/17)
The “People” factor must be addressed and continuously measured in order to increase effectiveness. Educating your employees/users on threats to your organization, safe web browsing practices, the hazards of clicking embedded links or opening attachments in unverified emails, and to scrutinize emails before opening them are just some of the basics. Your users are your first line of defense to prevent successful attacks and/or breaches.
In order to take your user’s education to the next level, you should conduct simulated phishing and social engineering exercises and campaigns. This will give your users “real world” experience in dealing with such attacks. Social engineering is still the most effective way that malicious individuals are able to access sensitive information. In fact, a recent survey “Nuix’s The Black Report: Decoding the Minds of Hackers” found that employee training was still a primary obstacle to hackers:
“What was interesting was, security countermeasures that historically organizations think are effective, the hackers laugh at and blow right by,” Pogue says. “And then other things that organizations don’t want to spend money on—like employee training—the hackers are like, ‘The most difficult thing for us to get around is well trained people.’”
The second facet of the defense in depth revolves around Process. In general, the processes around backups, incident response, breach notification, and disaster recovery should all be considered when strengthening a security program. For this particular scenario, the basic process that could have prevented an outbreak within your organization was a patch or vulnerability management. The patching of MS17-010 when it was released in March of this year would have closed the gap. Now we understand that is easier said than done. Some applications may “break” if patched due to unstable infrastructure or configuration, whereas other concerns revolve around high availability, making a reboot almost impossible. To tackle this, it is critical that organizations develop a multi- phased vulnerability management process. Deploying patches in a phased or tiered approach will help alleviate concerns that have kept patching from being a systematic, repeatable process – especially when a test environment is not present.
Technologies such as Security Information and Event Monitoring (SIEM), Data Loss Prevention or Intrusion Prevention Systems (IPS) can be leveraged to identify and even react to a ransomware attack as it is happening. We have seen that custom policy and rulesets can be utilized to alert in real time that there is something awry within the operating environment. Additionally, Network Access Control (NAC) platforms could make the isolation of infected devices quicker and easier.
Similarly, to the WannaCry attacks in May, the world experienced another massive cyber-attack in June; Petya. This attack caused numerous issues for healthcare organizations across the U.S. A Hospital in West Virginia was forced to rebuild all their computer hard drives as they were unable to access data and they needed to provide clean access to their EMR. Nuance Communications, a major provider of dictation services, was also impacted by the attack which impacted physician documentation across the country. The impact of these attacks serves as another reminder of how the fundamentals of a cybersecurity program are so crucial to protecting patient data.
Medical devices are a critical part of providing patient care in today’s technologically-connected healthcare industry. You would be hard pressed to find a hospital or health system that does not have hundreds to thousands of medical devices in use providing a variety of functions. Not unlike how the EMRs of the past were developed, the medical device industry has been slow to adopt safe security practices in design and implementation of these devices. Even today, we find devices that are using unsecure protocols or unsupported operating systems like Windows XP during our risk analysis process.
Couple that with the fact that healthcare environments have shifted from a homogenous makeup consisting of primarily a single OS, monolithic structure, reactive security approach and signature- based security tools/technologies to a more heterogeneous makeup where we see variety of operating systems, different types of devices (including IoT devices), cloud-based applications and services and behavioral-based security tools/technologies. The more complex our IT environments become, the more complex the risks to the data and patients becomes.
A 2015 report* by Raytheon & Websense suggests that “up to seventy-five percent of hospital network traffic goes unmonitored by security solutions out of fear that improperly configured security measures or alarming false positives could dramatically increase the risk to patient health or well- being.” Even if that number is on the smaller side, like twenty-five percent, the industry’s security technologies would be missing a considerable amount of data. Are we capturing the necessary data to gain the insight of where our medical devices are and more importantly – what behavior are they demonstrating? Is it normal?
With an increasing number of connected medical devices, medical IT networks are becoming more complicated. Typically, neither the IT department nor the Clinical Engineering teams within a healthcare organization have the necessary visibility and risk assessment tools, making the unprotected medical devices one of the weakest spots in a medical facility’s infrastructure. The lack of clear definition surrounding who owns the problem (CE vs. IT) has produced a situation where one of two things happens:
THE FIRST AND HARDEST STEP in addressing these security-related issues is gaining visibility. Gaining the required situational awareness and visibility is two-fold. The first is insight into what devices are operating within your environment. This is by far the most difficult to overcome. Our experience has shown that we typically can’t get two people in the same organization to agree on how many devices are connected in their environment. What makes it so hard is the dynamic nature in which devices are introduced and removed from the environment. It is imperative that organizations develop processes to gain the required visibility in order to gather actionable intelligence based on the associated risk. The next part of the visibility equation is acquiring the situational awareness into what vulnerabilities each unique device presents to the operational environment. Much like gaining the insight into which devices are on your network, organizations need to develop and implement processes to discover and validate vulnerabilities to their medical devices. Unfortunately, it doesn’t stop there. Once validated vulnerabilities are identified, the organization must evaluate the associated risk. Only then can decisions be made about the appropriate actions to address the risk.
THE SECOND STEP is the establishment of clear lines of ownership and communication. As previously mentioned, medical devices seem to live between the IT department and Clinical Engineering. To best address the management of these devices, the management/ownership needs to fall squarely on one department’s shoulders with the latter acting in a supporting role. Unfortunately, we can’t tell you who that department should be because each organization is unique in its allocation of resources (people, time, funding). In turn, the organization needs to make that decision based on their individual circumstances but it is critical that the decision is made and it is clear.
A THIRD consideration in addressing medical device security is compensating controls. Since the manufacturers are still playing catch-up with addressing the security portion of their devices it is critical that healthcare organizations institute compensating controls to reduce the identified risk or close the known vulnerabilities of medical devices. This could come in the form of a logical network separation or security technologies with unique controls that harden the environment in which the medical devices operate.
THE FOURTH is leveraging technologies where appropriate to automate the management of medical devices. Thankfully, the industry is now starting to see technologies come to market that can accomplish the work outlined above in a more efficient and automated fashion. The investment into a technology that can gain an organization visibility into the devices on their network and their associated vulnerabilities (where risk can be ascertained) and assist in remediating will provide tremendous value in closing the security gaps with regards to medical devices.
So far in 2017, OCR announced the first ever HIPAA settlement based on the untimely reporting of a breach of unsecured PHI as well as the first ever settlement involving a wireless health service provider. While these are firsts from an OCR settlement perspective, both may have been avoided if basic Risk Assessments had been completed and the appropriate policies and procedures implemented.
The first OCR settlement underlines the importance of policies and procedures including those that address the time requirements for Breach Notification. OCR’s investigation revealed that the health system failed to notify, without unreasonable delay and within 60 days of discovering the breach, each of the 836 individuals affected by the breach, prominent media outlets (as required for breaches affecting 500 or more individuals), and the OCR.
The second settlement highlights that not understanding HIPAA requirements creates risks, as this entity was unable to produce final policies and procedures during OCR’s investigation. Some were not fully implemented while others were still in draft form including those regarding the implementation of safeguards for ePHI.
OCR has continued to pursue settlements aggressively and is on pace to almost double the amount of settlements in 2017 as compared to 2016. Through the first five months of 2017, OCR has reached over $17M in settlements compared to just over $23M in full year 2016. Furthermore, OCR has already reached nine settlements thus far this year compared to 13 in all of 2016.
HEALTH CARE INDUSTRY CYBER SECURITY TASK FORCE
For over a year the Health Care Industry Cybersecurity Task Force (Task Force) has been charged with developing a Report outlining the growing challenges the healthcare industry faces when securing and protecting itself from cybersecurity incidents. The 21-member Task Force was the result of the Cybersecurity Act of 2015 (the Act) and is comprised of top professionals from across the industry (providers, payers, device manufacturers, security professionals, federal agencies, etc.) both private and public sector. As part of the Act, Congress asked the Task Force to accomplish six tasks:
(A) Analyze how industries, other than the healthcare industry, have implemented strategies and safeguards for addressing cybersecurity threats within their respective industries;
(B) Analyze challenges and barriers private entities (excluding any State, tribal, or local government) in the health care industry face securing themselves against cyber attacks;
(C) Review challenges that covered entities and business associates face in securing networked medical devices and other software or systems that connect to an electronic health record;
(D) Provide the Secretary with information to disseminate to healthcare industry stakeholders of all sizes for purposes of improving their preparedness for, and response to, cybersecurity threats affecting the healthcare industry;
(E) Establish a plan for implementing title I of this division, so that the Federal Government and healthcare industry stakeholders may in real time, share actionable cyber threat indicators and defensive measures; and
(F) Report to the appropriate congressional committees on the findings and recommendations of the task force regarding carrying out subparagraphs (A) through (E).
On June 2, 2017, the Task Force released the “Report on Improving Cybersecurity in the Health Care Industry” (the Report) to Congress fulfilling the statutory mandate. The Task Force collected 151 potential risks (68 confidentiality risks, 30 availability risks, 30 integrity risks, and 23 patient safety risks). Fifty-five percent of these potential risks related to the loss of Protected Health Information (PHI) which Covered Entities and Business Associates are charged to protect under HIPAA regulation. The detailed Report can be found on the Fortified Health Security website under resources.
“Covered entities must not only make assessments to safeguard ePHI, they must act on those assessments as well,” said OCR Director Jocelyn Samuels. “OCR works tirelessly and collaboratively with covered entities to set clear expectations and consequences.”
The Report paints a clear picture of a complex industry that has rapidly digitized in the last ten years with many interconnected data points running on an outdated infrastructure creating a wide surface area for cyber-attacks. The balance between providing real-time data to physicians at the point of care in a minimally disrupted manner, coupled with the charge for interoperability, has left the healthcare market more connected and more vulnerable to attacks than ever before.
Furthermore, the Report states that most healthcare organizations lack sufficient financial resources, struggle with retaining in-house information security expertise, don’t have the infrastructure to identify and track threats – much less analyze and take action based on the information — and are likely running unsupported legacy systems that cannot easily be replaced. These challenges are only exemplified by the fact that most health systems run on single digit margins forcing some organizations to choose between funding critical patient care or cybersecurity initiatives. These dynamics, combined with the increased sophistication of bad actors, have the Task Force portraying a healthcare industry in need of immediate action. The Report identifies six imperatives along with 27 recommendations and 104 action items. The imperatives are:
The Report calls for the implementation of all recommendations to increase awareness, better manage threats, reduce risk and vulnerabilities, and implement protections not widely adopted across the healthcare industry. While all the recommendations in the Report provide value to the cybersecurity posture of healthcare, and we encourage you to read the entire Report, there are several themes that caught our attention.
The Report suggests that there should be a single leader responsible for coordinating all healthcare cybersecurity programs and initiatives both within and outside of the Department of Health and Human Services (HHS). The recommendation is that The Health Care Cybersecurity Leader would work within HHS, externally with other federal agencies that impact healthcare, and with other healthcare related groups. The general premise is that this approach would reduce duplication of efforts and provide clarity, as well as better guidance around cyber risk and threats.
Given the diversity and complexity of the healthcare eco-system, which must support not only patient records but medical devices, this approach would allow one individual to look at cyber risks more comprehensively and be positioned to have a greater impact on the overall risk to the industry. Having the right individual charged with the coordination of initiatives across multiple government agencies which impact healthcare cybersecurity and balancing the ever-changing threat to PHI would likely increase our ability to respond as an industry and lead to an overall reduction of cybersecurity risk as an industry.
The Report suggests that a single cybersecurity framework be build upon the minimum standard of security required by the NIST Cybersecurity Framework and the HIPAA Security Rule. Although the NIST framework is not healthcare-specific, it does provide a solid foundation for assessing cybersecurity risk and combing the HIPAA Security Rule with NIST would provide a comprehensive framework for accessing healthcare specific risk.
Taking the step to provide a single framework would enable a unified lexicon for the healthcare industry as well as provide unified standards, guidelines, and best practices. This would make the management of cybersecurity risk across the entire healthcare spectrum much more manageable and measurable. As predicted by Fortified in the 2016 Horizon Report, this Report further encourages the move to a National Cybersecurity Framework specific to healthcare.
*Sources
*“Report on Improving Cybersecurity in the Health Care Industry”, Recommendation 1.1
**“Report on Improving Cybersecurity in the Health Care Industry”, Recommendation 1.2
The Report defines legacy systems as those which may not have ongoing support from the hardware and software vendors to include both legacy medical devices and legacy EHR applications. The specific action item to healthcare delivery organizations regarding securing legacy systems outlines some best practices that should be adopted for all products.
The Report recommends that health delivery organizations:
(MedCERT) to coordinate medical device-specific responses to cybersecurity incidents and vulnerability disclosures** Network connected medical devices represent a significant vulnerability for most health systems as outlined later in the Horizon Report — so much so that the Report frames this recommendation up as an interest of national security. The Report also describes “a market dynamic whereby healthcare providers have shouldered an inordinate amount of the burden even when actions needed to improve security in the device have been outside their control.”
MedCert would be comprised of experts including hardware, software, networking, biomedical engineers, and clinicians to enable a deep understanding of patient safety implications of medical device vulnerabilities. The team would be a trusted entity charged with determining the “ground truth” regarding medical device vulnerabilities and proposed mitigations. If needed, this team could be deployed into the field to investigate a suspected or confirmed medical device compromise. Given the potentially widespread and inherent impact to patient safety that an exploitable medical device vulnerability represents, the idea of creating a unified, proactive team of experts that would be at the ready represents a giant step forward.
Although some organizations may already have a Chief Information Security Officer (CISO) on the team while others may not, the focus for this recommendation centers around accountability and responsibility. Many organizations still view cybersecurity as an IT problem and have very poorly-defined roles and responsibilities for their cybersecurity leader. We experience this situation often with health systems and encourages organizations to empower the cybersecurity leader to implement a robust cybersecurity program including an appropriate level of oversight and enforcement.
*Sources
*“Report on Improving Cybersecurity in the Health Care Industry”, Recommendation 2.1
**“Report on Improving Cybersecurity in the Health Care Industry”, Recommendation 2.6
***“Report on Improving Cybersecurity in the Health Care Industry”, Recommendation 3.1
We hope this Mid-Year Horizon Report starts you on your path “from compliance to confidence” as we say at Fortified Health Security. Developing a strong cybersecurity posture does take time, energy and teamwork, and we welcome your feedback and perspectives at horizonreport@fortifiedhealthsecurity.com.

Chief Executive Officer
Dan L. Dodson serves as CEO of Fortified Health Security, a recognized leader in cybersecurity that is 100% focused on serving the healthcare market. Through Dan’s leadership, Fortified partners with healthcare organizations to effectively develop the best path forward for their security program based on their unique needs and challenges. Previously, Dan served as Executive Vice President for Santa Rosa Consulting, a healthcare-focused IT consulting firm, where he led various business units including sales for the organization. He also served as Global Healthcare Strategy Lead for Dell Services (formally Perot Systems), where he was responsible for strategy, business planning and M&A initiatives for the company’s healthcare services business unit. Dan also held positions within other healthcare and insurance organizations including Covenant Health System, The Parker Group and Hooper Holmes. Dan is a thought leader in healthcare cybersecurity and is a featured media source on a variety of topics including security best practices, data privacy strategies, as well as risk management, mitigation and certification. He was elected to the Association for Executives in Healthcare Information Security (AEHIS) Board of Trustees in 2022. In 2018, Dan was recognized as a rising healthcare leader under 40 by Becker’s Hospital Review and regularly speaks at industry-leading events and conferences including CHIME, HIMSS and HIT Summits. He served on the Southern Methodist University Cyber Security Advisory Board. Dan earned an M.B.A. in Health Organization Management and a B.S. in Accounting and Finance from Texas Tech University.

Vice President
Ryan focuses on increasing client security posture through driving collaboration between sales and operations teams. Prior to joining Fortified, he served as the Deputy Chief Information Officer for the New York State Division of Military and Naval Affairs and as a Director of a security and privacy healthcare IT consulting practice, in addition to working in the information security office for organizations such as MetLife and Memorial Sloan-Kettering Cancer Center. He holds an M.B.A. from Norwich University, as well as Certified Information Systems Security Professional (CISSP) certification and is a HITRUST Common Security Framework (CSF) certified practitioner.