Horizon Report
The state of cybersecurity in healthcare

Cybersecurity continues to occupy the top priority spot for most healthcare IT teams and is typically one of the top five overall priorities for an entire organization. Because of this, cybersecurity investments are on the same list as clinical investments, competing for the same budget dollars. CIOs and CISOs must now appropriately position cybersecurity investments as a patient safety need and highlight how cybersecurity weaves through every initiative within the healthcare organization.
A data breach could cost your organization $408 per record and cast anegative impression on your brand.
The reason our team produces the Horizon Report twice a year is that we are passionate about our vision to strengthen the cybersecurity posture of healthcare. Sharing data, best practices, and the insights we gain from working with hundreds of healthcare organizations is a cornerstone of one of our core values: collaboration. This passion also shows up in the work we do and in the industry recognition we receive. Thanks to our clients and the work our team achieved this year, Fortified Health Security was recognized by Frost & Sullivan as well as Black Book for our industry leadership in connected medical device security.
My hope is that the Horizon Report builds awareness about threats and provides valuable insight for your cybersecurity program. We welcome your feedback and perspective at horizonreport@fortifiedhealthsecurity.com. Enjoy.
Regards,

Dan L. Dodson
It is imperative that your multi-pronged security program is designed with security fundamentals, anchored in accountability, and driven by discipline. Oftentimes, security teams within healthcare organizations become distracted with special projects or new technology and abandon the daily, weekly, or monthly actions required to continuously execute the appropriate security fundamentals. In many cases, healthcare organizations have poorly implemented technology or lack the expertise to manage sophisticated security tools over time. This is a wide-spread issue magnified by organizations’ difficulties in securing adequate resources.
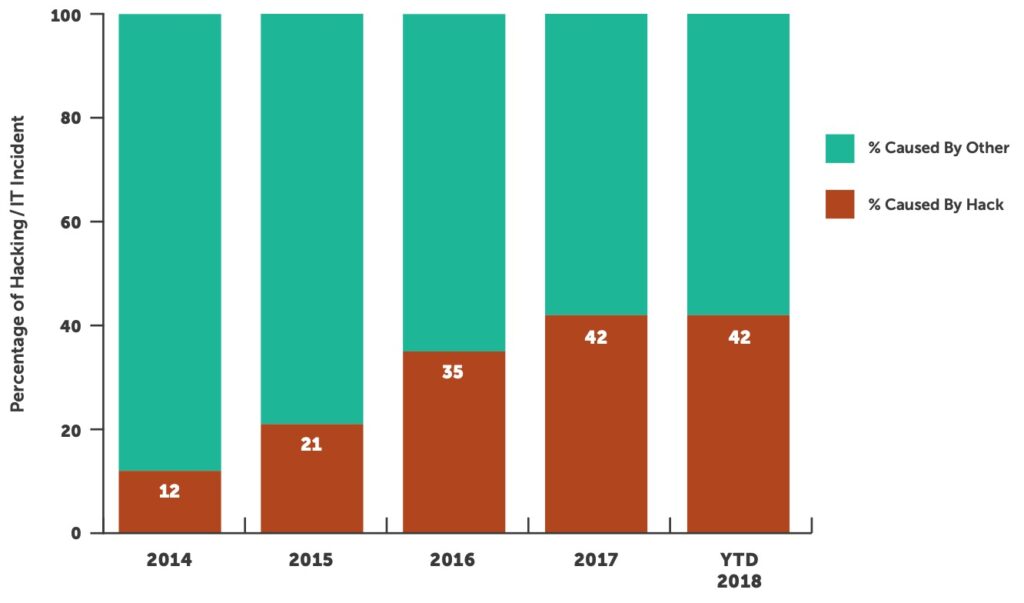
Don’t be fooled by the perceived value of technology as your actual level of protection may be less. It may be significantly underperforming expectations, especially if it has not been properly implemented or managed. Making multiple security technologies work in concert with each other and continuously managing them is critical to decreasing your chance of a large-scale breach caused by hacking.
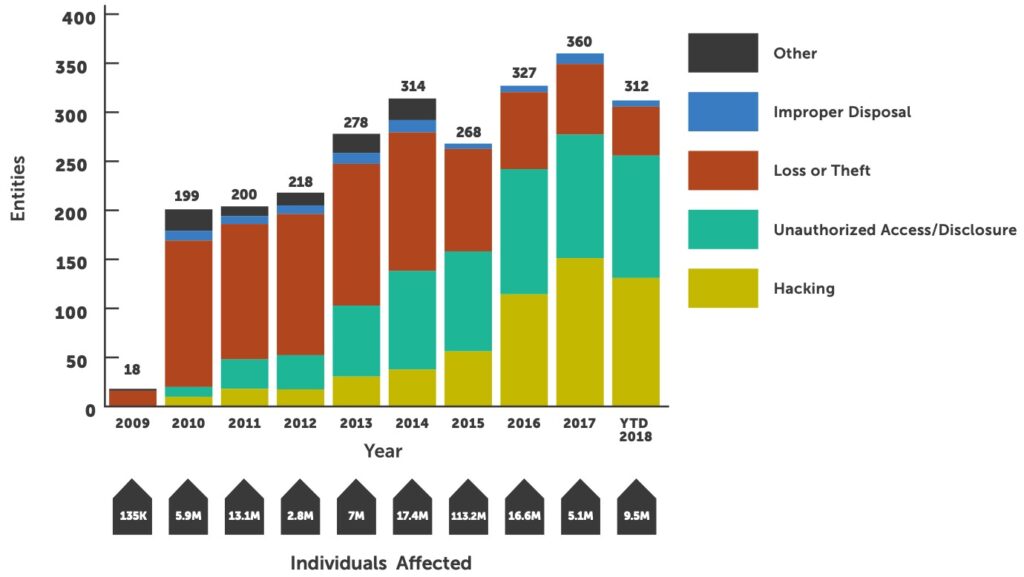
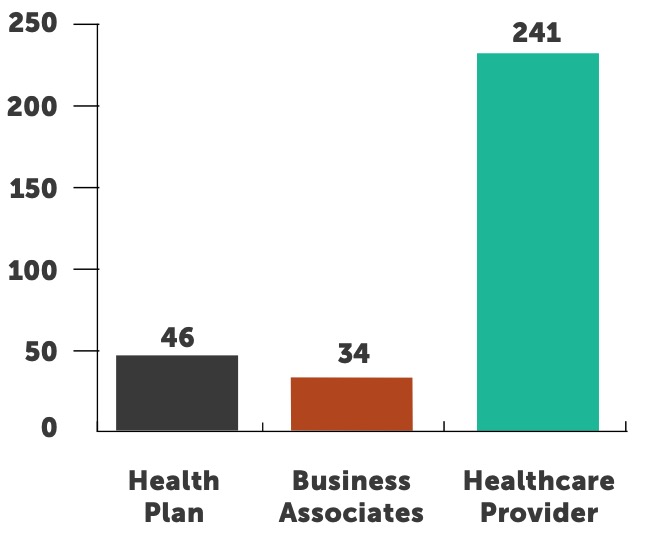
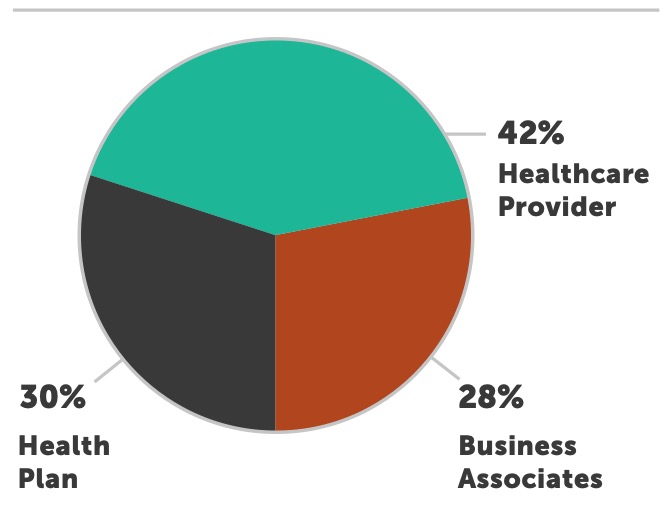
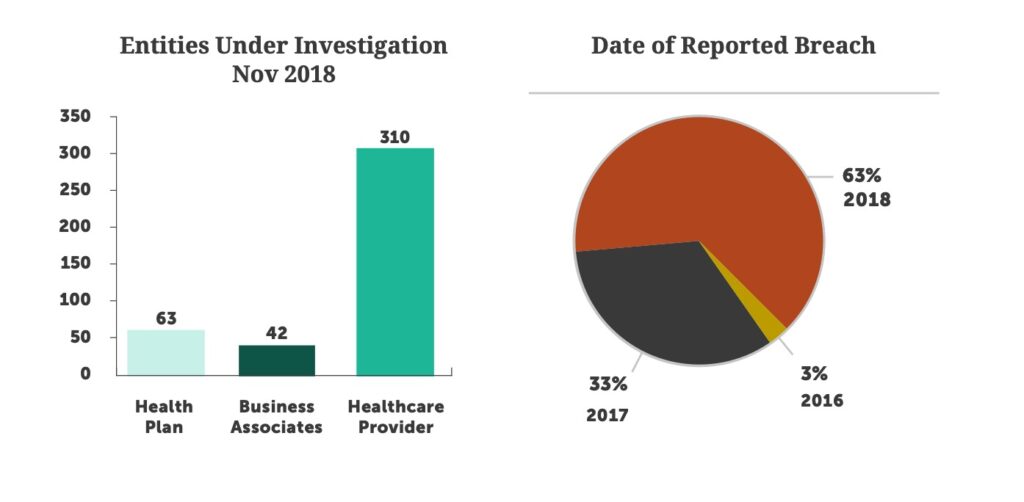
Healthcare provider organizations were the most targeted and successfully breached entities for the 10th year in a row. Over 74% of all reported breaches occurred at provider organizations, down from 80% in 2017. Providers have experienced over 241 breaches this year; we expect that number to climb to over 270 by end of year.
1 Source: https://ocrportal.hhs.gov/ocr/breach/breach_report.jsf|
2 Source: U.S. Department of Health and Human Services Office for Civil Rights
2018 marks the largest year of fines issued by the U.S. Department of Health and Human Services, Office for Civil Rights (OCR), with a total of almost $25 million. This includes the $16 million settlement paid by Anthem, Inc. for its reported breach in 2015, which eclipses the previous settlement high of $5.55 million paid by Memorial Healthcare System in 2017.2
It can take years for OCR to complete its investigation of a reported breach, causing a healthcare organization to spend significant time and resources responding to inquiries throughout the process. Identifying risks is the first step, but building and successfully executing a comprehensive corrective action plan is a requirement in the eyes of OCR. Doing this in tandem with an annual risk assessment based on a proven framework helps expedite investigations.
It is important to note that HIPAA is written in such a way that a certain level of interpretation is required; the regulations don’t provide black and white guidance on the steps your organization must take to fully comply. Part of the rationale in writing regulations this way is so that a single policy can encompass organizations of all sizes and scale, from billion-dollar health systems to small business associates.
Be sure your organization understands how it will be evaluated or viewed when compared to others in your peer group. The strength of your program will be judged based on acceptable best practices for an organization of similar size and scale. Regional health systems will be compared to other regional health systems, large IDNs to other large IDNs, and small doctor practices to other small doctor practices. This allows for a more reasonable set of accepted security practices based on your organization’s market position. You should consider what your peer group is doing with their security programs to ensure you are building, resourcing, and executing a security program that meets your needs. Every healthcare organization is at a different point in its security journey, and what is most important is that you assess risk, identify reasonably anticipated threats, create a plan, and continue to take reasonable action to improve your security posture.
In response to reported breaches, there were 415 active OCR investigations underway at the end of 2018, and 75% of them were with provider organizations. The majority of the investigations were in response to breaches reported in 2018, but 36% of investigations were in response to breaches reported over 12 months ago. The impact of a breach on an organization extends well beyond the initial shock and can leave a lasting impact on your organization. It is important to assess risks annually, execute on security fundamentals, and measure progress over time. As simple as this sounds, many health systems still lack a disciplined approach to managing their cybersecurity posture.
When speaking with healthcare organizations throughout 2018, three major topics consistently came up in almost every discussion:

Given that the Information Systems Audit and Control Association (ISACA) estimates a global shortage of 2 million cybersecurity professionals by 20193 , healthcare organizations are struggling to compete for the right resources to execute their security programs.

Vulnerabilities related to medical devices is not a new topic, but advances in new technology and an increased threat landscape have many health systems taking steps to better protect their connected medical devices.

While numerous health systems have adopted the Health Information Trust Alliance (HITRUST) framework for assessing risk, many are seeking certification to bring validation to their cybersecurity programs.
Healthcare organizations should hold frequent training sessions on security awareness, especially when employees are working remotely. IT and cybersecurity teams might hold training when you notice a common issue, receive a memo about a cyber threat in your industry, or start using a new program. The key is to keep employees in the loop, so they can avoid common errors and security pitfalls.
As healthcare organizations cope with the effects of the COVID-19 pandemic, IT departments are likely feeling the strain. A remote or hybrid workforce presents a wider spectrum of cybersecurity threats. By developing clear best practices for remote work and proactively managing their security programs, healthcare organizations can safeguard their networks from malicious actors. And of course, healthcare cybersecurity companies can assist you in prioritizing network vulnerabilities, mitigating risks, and safeguarding sensitive patient information.
Attracting, training, and retaining top cybersecurity talent may well be the biggest challenge facing healthcare organizations today as it pertains to building out their security programs. Having access to experienced cybersecurity talent is the foundation of any solid security program because human interaction is required to:
Recognizing the importance of people to any successful security program, CISOs and IT leaders across the healthcare industry find themselves squarely in a human capital battle with large corporations from all verticals. Typically, non-healthcare organizations have bigger security budgets, more advanced security technologies, more upward mobility for resources, and higher pay rates. This battle is felt across security staff, from executive leadership to analyst positions, and hits healthcare organizations coast-to-coast.
Executing security fundamentals tends to take a backseat while security leadership focuses on solving the human capital problem. Healthcare organizations may wait to start projects, implement new security controls, or pause the day-to-day execution of their security program altogether until a certain open position is filled. This increases risk and leaves healthcare organizations more vulnerable to attacks. After months of searching, organizations may successfully fill an open position only to find themselves with another hole. Someone else from the security team may have left or the newly acquired team member may not have the expertise required to manage the security tools previously implemented by the organization. This forces organizations to go back to the front lines of the cybersecurity human capital battlefield.
Unfortunately, we expect this battle to intensify in 2019 as demand for cybersecurity resources increases across all verticals and as the threats continue to strengthen. The looming question facing security and IT leadership is “are we fighting the right battle?”
Should your organization continue to fight a battle you may never win or are you better off focusing on patient care and seeking an alternative approach to managing your security program over time? Having a core group of resources to execute certain functions of your security program will certainly always be required, but alternative approaches exist to better equip your network, IT and security teams to tackle the battle you should be fighting: protecting valuable patient data from bad actors. Don’t let your organization’s cybersecurity program stall while you’re focused on human capital because, rest assured, our adversaries aren’t standing still.
Security risks associated with connected medical devices remain a top concern for leaders in healthcare organizations. Regulatory conversations continued in 2018 and some progress was made to better equip future released devices, but current in-market devices present the largest risk. The Food and Drug Administration (FDA) regulates over 190,000 devices manufactured by more than 18,000 firms in more than 21,000 facilities worldwide.4
Many devices already implemented across the healthcare eco-system are largely unpatched, may utilize hard- coded passwords, and run outdated operating systems. These already in-market medical devices provide a massive surface area for attack by adversaries and present the largest risk. Since medical devices do not have a regulated useful life, they typically are not replaced unless they are no longer functioning clinically. This leaves health systems with thousands of potentially vulnerable devices. Segmenting medical devices onto their own network remains best practice, but the speed at which medical devices are connecting to networks is outpacing many organizations’ ability to adequately segment these devices.
Besides the challenges that come with a large volume of devices and a great variety of device manufacturers, there is a unique market dynamic between medical device manufacturers and health systems that makes managing the security of connected medical devices exponentially more difficult. Every device manufacturer communicates vulnerabilities differently and some require patches to be pre-approved or the health system risks voiding the device’s warranty. The variation in manufacturer processes and devices makes it nearly impossible to resource an effective connected medical device security strategy.
These market dynamics mixed with technical limitations and internal politics present the following challenges for organizations developing a robust cybersecurity program for connected medical devices:
Under current regulation, responsibility for in-market device security falls squarely on the shoulders of health systems.
There has been significant progress made with technology focused on securing connected medical devices in the last few years. This is primarily driven by the $100 million in capital poured into a handful of technology vendors that have built solutions powered by machine learning and artificial intelligence to address device security. These companies all differ in features and functionality, but in the simplest form, they successfully identify and profile all the medical devices within your environment. From there, their feature set and security functionality differs greatly.
We believe the healthcare industry has an opportunity to tackle the challenge of medical device security. That’s why we’ve created a six-step program that aligns people, process, and technology to solve your business problems and drive successful outcomes surrounding connected medical device security. This program is continuous, actionable, scalable, and focused on reducing surface exposure and overall risk.
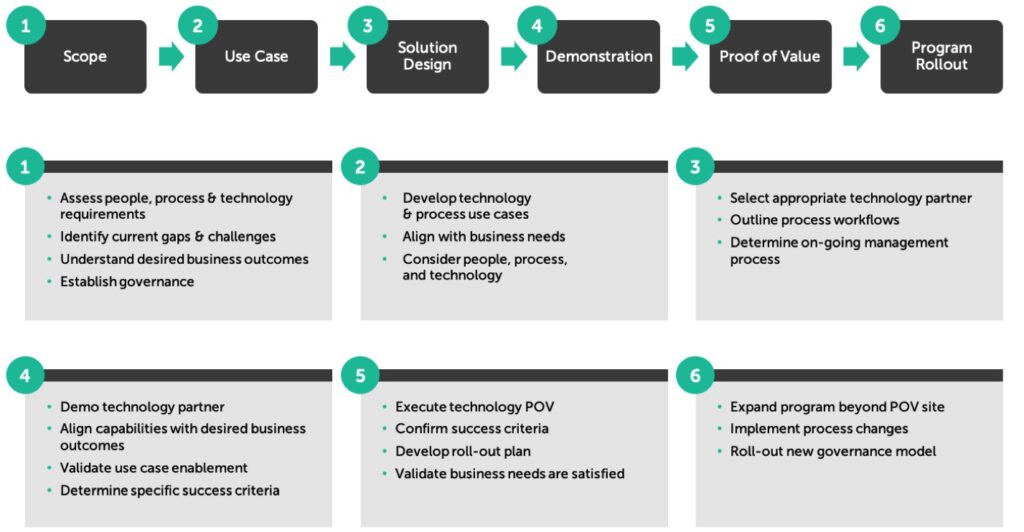
Like all major security initiatives, in order to maximize your investment, it is critical to ensure your organization is prepared to operationalize advanced technologies so the business outcome you desire becomes reality.

HITRUST certification enables organizations to identify risks through a data-driven approach and develop meaningful action plans to help mitigate these risks. It also can help organizations cut down on the number of vendor-requested risk assessments they must complete annually, as many vendors accept HITRUST certification in lieu of their own risk assessments.
Don’t underestimate the lift required to become HITRUST certified. The journey requires significant internal resources, regardless of what any vendor tells you. Our experience is that certification takes an average of 9 months to complete but can be a multi-year process depending on your starting point. Below are some tips to keep in mind when embarking on the HITRUST journey:

Double-Digit Increase in Breaches: Healthcare will experience a 10-20% increase in the number of entities breached, with providers being the most targeted and exploited segment.
So how did we do? A review of the OCR breach notification data shows the healthcare industry experienced a 13.6% increase in the number of entities reporting breaches over 2017. Between January and October 2017, 360 entities reported a breach versus 312 for the same period in 2018. Healthcare providers represented 74% of reported breaches, an increase of 5%, with 218 provider entities reporting a breach in 2017 and 229 reporting a breach in 2018.1
More Variants of WannaCry Ransomware: In May 2017, many companies around the world fell victim to the WannaCry ransomware attack. Other variants of WannaCry (like NotPetya) soon followed. With unpatched systems still prevalent and vulnerable to WannaCry, it is safe to assume hackers will release additional, more intelligent variants of WannaCry in 2018.
Breaches due to Business Associate Neglect (Third-Party Risk Management Failure) on the Rise: In 2017, OCR has identified at least 18 breaches due to business associate neglect and, more importantly, failure by the covered entity to manage that risk. Healthcare-covered entities will continue to experience risk and possible breaches in 2018 unless effective business associate risk management programs are established.
So how did we do? In 2017, 5% or 18 of the 360 reported breaches included business associates. This quadrupled in 2018 to 24% of reported breaches, or 74 of the 312 at the time of this report. This staggering increase highlights the importance of managing business associate risk.1
Increased Threat to IoT Devices: Medical devices constitute a large number of Internet of Things (IoT) devices currently connected to healthcare networks around the world. In October 2017, newer, more powerful versions of IoT malware (“Reaper” and “IoTroop”) were discovered in the wild. The malware spreads very easily through IoT devices with little to no security. We should expect this malware to be seen in more healthcare IoT devices in 2018 — if they’re not there already.
1 Source: https://ocrportal.hhs.gov/ocr/breach/breach_report.jsf
4 Source: FDA Medical Device Safety Action Plan: Protecting Patients, Promoting Public Health
5 Source: https://hitrustalliance.net/hitrust-csf/
6 Source: https://www.welivesecurity.com/2018/05/10/one-year-later-eternalblue-exploit-wannacryptor/
7 Source: https://chimecentral.org/chime-klas-survey-measures-providers-confidence-in-medical-device-security-programs/
8 Source: https://www.medcrypt.co/medcrypt-vulnerability-analysis-whitepaper-1.pdf
As healthcare IT teams face limited budgets, resource constraints, and difficulty defending their networks against escalating threats, security vendors continue to claim to have the “silver bullet” to solve all your problems. Before evaluating the next security technology solution, we recommend you focus internally, as there is one constant: employees are your biggest security risk. It is important to take steps to protect your organization from employee actions, whether malicious or accidental.
It is commonly said that people, or users, are an organization’s most important asset, and yet they are almost impossible to secure because…
YOU CAN’T PATCH THEM
YOU CAN’T RECONFIGURE THEM
YOU CAN’T HOLD THEIR HANDS
Industry best practice recommends considering people, process, and technology when implementing safeguards to protect users from themselves. But, where should you begin?
User hygiene is the most important control you can put in place. This starts with an effective security and awareness program. Establishing an effective program is more cultural than financial. It is important that user education is championed by top leadership and transcends throughout every layer of the organizational chart.
Our experience has shown that gamification in the implementation of your security and awareness program provides immediate results as the competitive nature of individuals always seems to bubble to the top. The program should be multi-faceted and not just a point-in-time training course or email blast. The components of a well-rounded program are outlined below. Some are much easier to implement than others and most can be operationalized at minimal cost. It is the necessary culture change that is typically the major roadblock at most healthcare organizations.
Like all major security initiatives, in order to maximize your investment, it is critical to ensure your organization is prepared to operationalize advanced technologies so the business outcome you desire becomes reality.
Make employees aware of the security risks in your organization. Provide a communication mechanism when they see a threat. Instill a sense of trust and action from security. Offer visibility into the security controls in place.
Obtain executive support. Select modules that cover the biggest security risks. Ensure you test and capture metrics. Do not make it a laborious effort for users.
Test the enterprise regularly. Make it competitive within organizational departments. Use current threats when designing your campaign. Provide instant feedback to users.
Use threat intelligence from your security team. Create and communicate a threat dashboard. Provide users visibility to the controls in place.
Propagate threat information to ALL users. Create security news bulletins or alerts. Provide additional references for information. Increase awareness during high-threat times (i.e., holidays, Tax Day, Black Friday).
Your users are busy in their day-to-day work, serving patients and providing care. Therefore, effective cybersecurity programs must implement technologies that detect and stop threats before they reach users in the first place. Implementing the right security technologies in conjunction with your security and awareness program is how you mitigate these risks to an acceptable level. This next step can require additional investment in people, process, and technology, so it is important that you first maximize the functionality of all security technologies previously implemented.
Email and web browsing are the top platforms used by cybercriminals to breach your organization’s data. The available technologies are plentiful, and you need to choose them carefully based on your organization’s risk reduction goals. It’s also important to make sure you have the resources to manage and monitor them, as none are turnkey or “set it and forget it” technologies.
Below is a list of technology categories that support a well-rounded security program. Determine which technologies you need to address risk in your organization based on recent risk assessments, audits, previous security incidents, and/or breaches.
Like all security-related initiatives, it takes dedication, support, and a willingness to change organizational culture to successfully protect users. Keep in mind that security is a journey and incremental improvement is best. Work with your organization to drive the right culture change, and you can successfully lower risks associated with user behavior.
Cybersecurity Outlook 2019
1
2
3
4
When speaking with healthcare organizations throughout 2018, three major topics consistently came up in almost every discussion:

You can’t protect what you can’t see. Creating a security program that is powered by technology and appropriately operationalized can give you the visibility you need to better protect your organization. Visibility will ultimately lead to better protection and lower overall risk.

This is very difficult in healthcare due to the dynamic clinical user base. Organizations that practice least privileged access management significantly change their risk profile when the process is powered by technology and successfully supported.

Healthcare executives often look for a silver bullet, which forces organizations to purchase technical point solutions that tend to be under-implemented and under-supported. This leads to the misperception that you are more protected than you are. Don’t forget to consider how you monitor and manage technology over time.

Compliance is not security. However, a properly implemented security program usually meets compliance. Healthcare organizations should focus on creating a “defense in-depth” strategy that is adequately supported and grounded in an approach that encompasses people, process, and technology.

Chief Executive Officer
Dan L. Dodson serves as CEO of Fortified Health Security, a recognized leader in cybersecurity that is 100% focused on serving the healthcare market. Through Dan’s leadership, Fortified partners with healthcare organizations to effectively develop the best path forward for their security program based on their unique needs and challenges. Previously, Dan served as Executive Vice President for Santa Rosa Consulting, a healthcare-focused IT consulting firm, where he led various business units including sales for the organization. He also served as Global Healthcare Strategy Lead for Dell Services (formally Perot Systems), where he was responsible for strategy, business planning and M&A initiatives for the company’s healthcare services business unit. Dan also held positions within other healthcare and insurance organizations including Covenant Health System, The Parker Group and Hooper Holmes. Dan is a thought leader in healthcare cybersecurity and is a featured media source on a variety of topics including security best practices, data privacy strategies, as well as risk management, mitigation and certification. He was elected to the Association for Executives in Healthcare Information Security (AEHIS) Board of Trustees in 2022. In 2018, Dan was recognized as a rising healthcare leader under 40 by Becker’s Hospital Review and regularly speaks at industry-leading events and conferences including CHIME, HIMSS and HIT Summits. He served on the Southern Methodist University Cyber Security Advisory Board. Dan earned an M.B.A. in Health Organization Management and a B.S. in Accounting and Finance from Texas Tech University.

Chief Operating Officer
William Crank serves as Chief Operating Officer for Fortified Health Security where his responsibilities include enhancing the company’s services, delivery model, and security operations center. As a member of the executive committee, William works to streamline operations among the sales, solution architect, account management, and customer success teams in addition to continually enhancing Fortified’s expertise by attracting, training, and retaining top security talent. Prior to his role as COO, William was the chief information security officer (CISO) at MEDHOST, a provider of market-leading enterprise, departmental, and healthcare engagement solutions. He has decades of information technology and security experience that include managing the Information Security Risk Management (ISRM) team at Hospital Corporation of America (HCA), where he led a team of Information Security professionals who managed compliance and information security risk and developed and implemented an operational risk management model. William retired after serving 20+ years from the United States Navy. He currently holds multiple certifications in the areas of Information Security and Information Technology. William has also served as Sponsorship/Programs Director and Vice President of the Middle Tennessee chapter of the Information Systems Security Association (ISSA).