Horizon Report
The state of cybersecurity in healthcare

The U.S. healthcare market continues to face an increase in cybersecurity threats from bad actors, and it looks as if 2019 will top last year for the most breaches ever reported. With momentum on the side of our adversaries, it is important that we, as healthcare cybersecurity leaders, continue to focus on and execute security fundamentals. Oftentimes internal cybersecurity teams become sidetracked by other IT projects, and the daily requirements of a solid cybersecurity program get pushed to the side. This dynamic is playing out across the country, and coupled with a weak security training program, many organizations find themselves vulnerable. It is critical to remember the fundamentals when evaluating your cybersecurity program.
I see many of these challenges playing out in healthcare organizations of all sizes and financial strength. More money spent on security doesn’t necessarily mean more sophistication or a more mature security program. Know that you are not alone, and I strongly advocate for security professionals to communicate, network, and collaborate to help strengthen the cybersecurity posture of healthcare. My hope is that the Horizon Report builds awareness about the cybersecurity landscape in healthcare and provides valuable insight for your program. We welcome your feedback and perspective at: horizonreport@fortifiedhealthsecurity.com. Enjoy.
Regards,

Dan L. Dodson

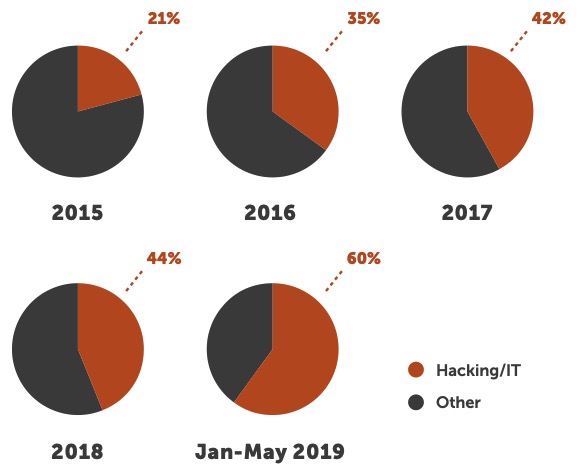
1 Source: BakerHostetler: 2019 Data Security Incident Response Report
2Source: U.S. Department of Health and Human Services Office for Civil Rights
1
2
3
4
THE GREAT UNKNOWN
Overall, most healthcare organizations invest more in cybersecurity today than they did a few years ago, but a challenge that remains is how to compare one organization’s security posture to another. This is important for two reasons. First, you need to understand what the return is on your investments, as capital tends to be limited and cybersecurity initiatives compete for clinical dollars in most instances. You should be able to demonstrate how investing in cybersecurity has reduced risk and enabled higher quality patient care. Second, based on the principle of reasonableness, current regulation compares one healthcare organization’s security program to that of its peers to determine overall effectiveness.3 So, understanding the maturity of your security program relative to others of similar size and scale is important.
This leaves many healthcare IT and information security leaders asking themselves: is my organization’s investment in cybersecurity positively impacting our security posture? Are we allocating our resources in areas that will have the greatest impact on our organization from a risk perspective? How does our security posture compare to that of our peers?
Welcome to the great unknown! Because multiple tools are being used within each security domain and there is no way to aggregate information meaningfully between the tools, it is no surprise that leaders are left with limited ability to provide confident answers to these critical questions.
3 Source: Federal Trade Commission, Data Breach on the Rise: Protecting Personal Information From Harm.
Prepared Statement before the Committee on Homeland Security and Governmental Affairs, U.S. Senate, Washington, D.C., (Apr. 2, 2014).
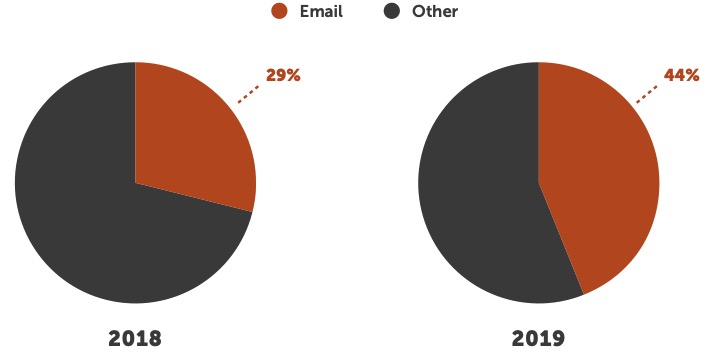
Healthcare organizations of every size and scope rely on email as a predominant business tool for both internal and external communications. Unfortunately, email is also a primary vector for network security breaches and cyberattacks. Recent statistics reveal that 92% of all malware is distributed from an email platform, with 93% of all phishing emails housing some type of malware.4
Healthcare data is some of the most highly coveted intelligence on the dark web, making it a primary target for cybercriminals on a global scale. It’s a trend that is only expected to grow in upcoming years, as an industry review predicted the cumulative number of ransomware attacks within medical enterprises will quadruple by 2020.5
Perhaps the most alarming malware statistic within the healthcare industry? A whopping 78% of people understand the risks associated with unknown email links but click anyway.6 Yes, some of these data breaches can be attributed to sheer curiosity or user inattentiveness, and some security lapses stem from users linking their corporate email accounts to outside (unsecured) third-party websites. However, many times healthcare employees are legitimately lured into believing that every communication in their inbox is authentic and secure, particularly if they use Microsoft Office 365 as their primary business collaboration and productivity tool.
As one of the most popular cloud-based business platforms, MS Office 365 often falls prey to a broad spectrum of cybercriminal activity; however, Outlook (its email module) has proven especially vulnerable. Much like other forms of cybersecurity malware, the already turbulent terrain of email threats is continuously (and rapidly) evolving. Hackers on a worldwide scale are designing and executing a wide range of increasingly sophisticated email scams explicitly devised to mimic real-life companies, events, and meetings so recipients will click.
These highly complex email attacks aren’t just fooling humans—they are also tricking our digital platforms. A recent analysis of MS Office 365 showed that the system demonstrated a “miss rate” greater than 9%, consistently allowing in a diverse range of emails containing the following:7
From faux board meeting invitations to fraudulent email cards over the holidays, MS Office 365 can inadvertently allow countless hoaxes into users’ inboxes, increasing the risk of a data breach with a single mouse click.
When sourcing specialized providers, it’s important to remember that not all outside healthcare cybersecurity services are created alike. Find a specialist that offers a comprehensive suite of strategies and customizable solutions to maximize complete compliance coverage and protection for all of your sensitive stored healthcare data. Key service components should include a wide range of anti-spoofing and link protection tools, such as:
Most healthcare organizations recognize the necessity of enabling multi-factor authentication, but some struggle to execute it due to the workflow impact. When putting this best practice in place, it is important to first identify who truly needs access to email outside your environment and who needs access inside the walls of the health system. From there you can determine the most effective way to deploy multi-factor authentication while limiting disruption to your current clinician workflow. Although this security feature may require a bit of a culture change, when deployed correctly, multi- factor authentication can have the biggest impact on your email security program.
Working with an experienced cybersecurity team that delivers agile and robust Microsoft Office 365 solutions can prevent a cyberattack, circumventing suspicious inbound activity to keep your healthcare facility’s operations moving forward at maximum momentum.
The good thing about Office 365 is it provides easy access to email for users anywhere in the world. The bad thing about Office 365 is it provides easy access to email for users anywhere in the world. Managing email in a responsible and effective manner means reducing cybersecurity risk while providing the right level of access required for employees to execute their jobs effectively.
4 Source: https://www.csoonline.com/article/3077434/93-of-phishing-emails-are-now-ransomware.html
5 Source: https://www.beckershospitalreview.com/healthcare-information-technology/healthcare-ransomware-attacks-to-jump-4-fold-by-2020-5-report-findings.html
6 Source: https://www.ena.com/phishing-scams/
7 Source: https://www.darkreading.com/cloud/office-365-missed-34000-phishing-emails-last-month/d/d-id/1330282

Chief Executive Officer
Dan L. Dodson serves as CEO of Fortified Health Security, a recognized leader in cybersecurity that is 100% focused on serving the healthcare market. Through Dan’s leadership, Fortified partners with healthcare organizations to effectively develop the best path forward for their security program based on their unique needs and challenges. Previously, Dan served as Executive Vice President for Santa Rosa Consulting, a healthcare-focused IT consulting firm, where he led various business units including sales for the organization. He also served as Global Healthcare Strategy Lead for Dell Services (formally Perot Systems), where he was responsible for strategy, business planning and M&A initiatives for the company’s healthcare services business unit. Dan also held positions within other healthcare and insurance organizations including Covenant Health System, The Parker Group and Hooper Holmes. Dan is a thought leader in healthcare cybersecurity and is a featured media source on a variety of topics including security best practices, data privacy strategies, as well as risk management, mitigation and certification. He was elected to the Association for Executives in Healthcare Information Security (AEHIS) Board of Trustees in 2022. In 2018, Dan was recognized as a rising healthcare leader under 40 by Becker’s Hospital Review and regularly speaks at industry-leading events and conferences including CHIME, HIMSS and HIT Summits. He served on the Southern Methodist University Cyber Security Advisory Board. Dan earned an M.B.A. in Health Organization Management and a B.S. in Accounting and Finance from Texas Tech University.

Chief Operating Officer
William Crank serves as Chief Operating Officer for Fortified Health Security where his responsibilities include enhancing the company’s services, delivery model, and security operations center. As a member of the executive committee, William works to streamline operations among the sales, solution architect, account management, and customer success teams in addition to continually enhancing Fortified’s expertise by attracting, training, and retaining top security talent. Prior to his role as COO, William was the chief information security officer (CISO) at MEDHOST, a provider of market-leading enterprise, departmental, and healthcare engagement solutions. He has decades of information technology and security experience that include managing the Information Security Risk Management (ISRM) team at Hospital Corporation of America (HCA), where he led a team of Information Security professionals who managed compliance and information security risk and developed and implemented an operational risk management model. William retired after serving 20+ years from the United States Navy. He currently holds multiple certifications in the areas of Information Security and Information Technology. William has also served as Sponsorship/Programs Director and Vice President of the Middle Tennessee chapter of the Information Systems Security Association (ISSA).