Horizon Report
The state of cybersecurity in healthcare

The healthcare industry is vulnerable not only because of the sensitive and valuable information it stores, but also due to the “always on” nature of its business and its need for constant data access. Cybercriminals use the simple fear of being locked out of data access to extort high ransoms from healthcare organizations that are under pressure to get their systems back up and running because patient lives are at stake.
Compounding the situation is the Internet of Things (IoT) and Bring Your Own Devices (BYOD) connecting to the network allowing new opportunities for malware to enter the healthcare environment.
Compounding the situation is the Internet of Things (IoT) and Bring Your Own Devices (BYOD) connecting to the network allowing new opportunities for malware to enter the healthcare environment.
Technology companies have recognized the need to bolster their cybersecurity defenses and are also joining in to help healthcare organizations strengthen their security posture. 2019 saw an increase in mergers, acquisitions, and investments by these companies to include or expand upon their cybersecurity capabilities.
This year, the Department of Health and Human Services (HHS) proposed modifications to both the Anti-Kickback Statute (AKS) and the Physician Self-Referral Law (often referred to as the “Stark Law”) that recognized the increased threat of cyberattacks due to digitization and connectivity. The proposed Stark Law changes would allow providers to accept technology-related donations essential to reducing the risk of a data breach or cyberattack.
As we enter 2020, disciplined strategies geared toward reducing risk over time are more important than ever before. Every organization needs a strategy that effectively balances people, process, and technology to navigate this difficult landscape.
An organization’s workforce is still its greatest cybersecurity vulnerability. Healthcare organizations must embrace a greater responsibility to help employees navigate cybersecurity best practices, identify possible phishing attacks, and remain vigilant to solve this immense global challenge. In doing so, they will create not just a more engaged and educated workforce, but also a more secure environment.
Although cyberattacks are getting more sophisticated and targeted, executing fundamental security practices remains key to sustaining a strong cybersecurity program. Organizations that remain disciplined and focused reap rewards over the long term. My hope is that the Horizon Report builds awareness about the cybersecurity landscape in healthcare and provides valuable insight for your program. We welcome your feedback and perspective at: horizonreport@fortifiedhealthsecurity.com. Enjoy.
Regards,

Dan L. Dodson
Previous trends that dominated healthcare cybersecurity continued throughout 2019, and bad actors have accelerated their attacks on healthcare organizations across the country. Ransomware and phishing wreaked havoc, disrupting patient care and costing organizations millions of dollars to remediate and recover critical systems. For the first time ever, more than 400 healthcare organizations reported a breach of 500+ patient records in a single year. Despite continued efforts to make improvements, many still struggle to stay in front of cybercriminals due to limited budgets, human capital challenges, and alert fatigue. It is critical to develop and execute effective cybersecurity programs that are grounded in fundamentals, staffed correctly, and focused on risk mitigation.
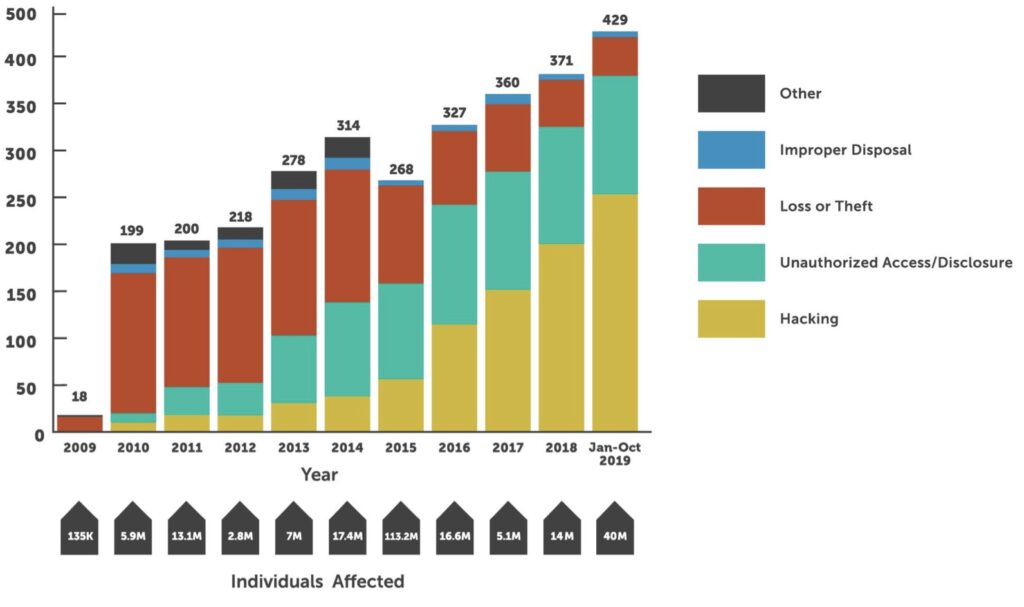
This marks the 10th year that the U.S. Department of Health and Human Services, Office for Civil Rights (OCR) collected and posted breach notification information to the public. 2019 also represents the greatest number of reported breaches in a single year. Through the first 10 months, the number of reported breaches increased 38% compared to the same period last year. In total, over 429 entities have reported a major breach so far, which already eclipses the 371 entities impacted in all of 2018. This equates to over 40 million individuals impacted by these reported breaches. We expect the number of entities reporting a breach to surpass 480 by the end of 2019.
Previous trends that dominated healthcare cybersecurity continued throughout 2019, and bad actors have accelerated their attacks on healthcare organizations across the country. Ransomware and phishing wreaked havoc, disrupting patient care and costing organizations millions of dollars to remediate and recover critical systems. For the first time ever, more than 400 healthcare organizations reported a breach of 500+ patient records in a single year. Despite continued efforts to make improvements, many still struggle to stay in front of cybercriminals due to limited budgets, human capital challenges, and alert fatigue. It is critical to develop and execute effective cybersecurity programs that are grounded in fundamentals, staffed correctly, and focused on risk mitigation.
This marks the 10th year that the U.S. Department of Health and Human Services, Office for Civil Rights (OCR) collected and posted breach notification information to the public. 2019 also represents the greatest number of reported breaches in a single year. Through the first 10 months, the number of reported breaches increased 38% compared to the same period last year. In total, over 429 entities have reported a major breach so far, which already eclipses the 371 entities impacted in all of 2018. This equates to over 40 million individuals impacted by these reported breaches. We expect the number of entities reporting a breach to surpass 480 by the end of 2019.
1 Source: U.S. Department of Health and Human Services Office for Civil Rights
In the first 10 months of 2019, there were eight resolution agreements reached between OCR and healthcare organizations. Each agreement included a steep fine, averaging more than $1.6 million, as well as a multi-year corrective action plan that requires the organization to make improvements to its cybersecurity program.
According to HHS:
“A resolution agreement is a settlement agreement signed by HHS and a covered entity or business associate in which the covered entity or business associate agrees to perform certain obligations and make reports to HHS, generally for a period of three years. During the period, HHS monitors the covered entity’s compliance with its obligations. A resolution agreement may include the payment of a resolution amount.”
Prior to a resolution agreement, a multi-year investigation takes place, costing organizations time and resources. Currently, there are 571 organizations under investigation for incidents dating back to 2017.
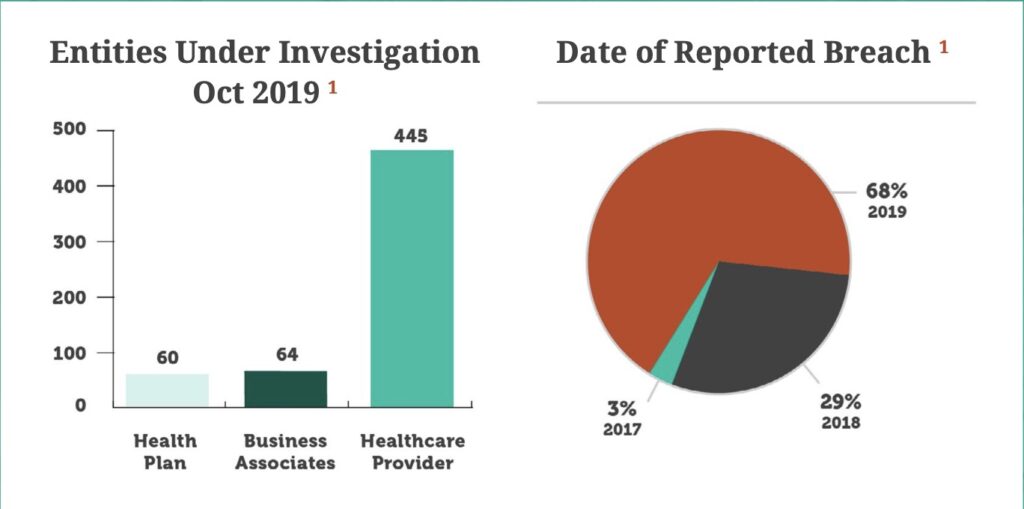
The impact of a breach at any healthcare organization extends well beyond the time it takes to regain full functionality of critical systems. These OCR investigations take a toll on the organization and prove to be a constant reminder of past incidents years after the breach is identified. Conducting an annual risk assessment and, more importantly, making progress against any corrective action plans are critical steps to simplifying the investigation process and potentially limiting fines. Healthcare organizations that take a disciplined, documented, risk-based approach to cybersecurity are more likely to avoid this process altogether. But, should they find themselves working with OCR, they will be in a much better place.
1
2019 has been a significant year for mergers and acquisitions in cybersecurity, as large companies sought to create more sophisticated platforms, and smaller businesses continued consolidation.
2
Ransomware is becoming a more commonly used tool in cyber crimes and can be carried out from anywhere in the world. Major healthcare systems were paralyzed this year by ransomware attacks.
3
HHS proposed changes to the Stark Law will allow providers to accept technology-related donations in an effort to reduce cybersecurity risk.
Mergers and acquisitions have always been a driving force throughout global technology sectors for a myriad of reasons. The continually evolving innovation landscape allows tech companies of every size, scope, and focus to align their resources with other innovative organizations in hopes of better leveraging synergies, driving corporate growth, and ultimately commanding a more significant share of the consumer market. As a result, technology companies continuously evaluate opportunities to strengthen their current product offerings, expand their technology stack into new areas, and in some instances, enter into entirely new market verticals. The cybersecurity technology market was influenced by these forces in 2019 with numerous investments and vendor consolidations.
In recent years, the alarming rise in worldwide cyberattacks and data breaches has prompted a noticeable upswing in cybersecurity mergers and acquisitions within the tech sector. The cybercriminal terrain across virtually every industry is both complex and ever-changing, making companies that specialize in cybersecurity highly desirable assets for technology-centric enterprises. Over the last year alone there have been several significant and strategic moves within the cybersecurity market.
Secondly, there is significant focus around securing the IoT, which includes non-traditional technologies. Medical devices continue to be one of the most vulnerable assets within a healthcare organization and are included in the larger IoT security market. There have been considerable advancements in machine learning, artificial intelligence, and behavioral analytics to assist in solving IoT security challenges and secure medical devices for many organizations. Of course, with advancement comes consolidation and investment. In 2019, there were many Silicon Valley-based companies that raised capital to advance their IoT technology and ramp up sales efforts. As for consolidation, Palo Alto, an organization known for its propensity to purchase leading startups, announced its intent to buy Zingbox3, an IoT security innovator. Furthermore, device visibility developer ForeScout Technologies acquired SecurityMatters4.
a company that specializes in network protection, variance identification, and device detection and monitoring solutions. Increased consolidation in the IoT cybersecurity market is expected over the next couple of years. Though there are distinct nuances to each deal, these mergers and investments collectively highlight the growing trend of larger companies using acquisitions to bolster their security offerings through product integration and enhancements, as well as to grow their client portfolios. However, big tech companies aren’t the only ones that benefit from aligning their resources and established enterprises with smaller security firms.
By expanding their existing suite of competencies to include cybersecurity solutions, technology organizations can do more than command additional market share. These companies are also uniquely equipped to better serve their customers, particularly those in the healthcare space. More importantly, this trend of acquisition is likely to continue for the foreseeable future, prompting CISOs and IT managers across the country to take a closer look at the advantages of working with a technology partner that provides services and solutions across several innovation niches, including network security.
The first thing many healthcare organizations think about in the current climate of mergers, acquisitions, and IPOs is “How will these changes impact my organization?” For the most part, there is little to no immediate impact following a merger, acquisition, or IPO. The real question is how the product will evolve or innovate over time. It is important to meet with your technology partners following the transaction to understand what their technology roadmap looks like. Remember that in some instances, the new owner may need time to finalize the roadmap. The best course of action is to ask questions with an understanding that it may take time to get the real answer. Additionally, it may be the ideal time to assess your existing technology infrastructure and current cybersecurity practices to ensure all internal programs focus on three mission-critical components: people, process, and technology.
Partnering with a managed services organization can immediately simplify the decision-making process. Rather than taking the time to vet individual technology companies for each required element of your security program, healthcare organizations can benefit from engaging a managed services partner to evaluate, select, implement, and manage the right technology. With the technology vendor landscape evolving, this expertise may be more important than ever before.
Ransomware has long proven a major threat to healthcare organizations across the U.S. Marked by the release of malware that locks a digital environment, a ransomware attack prevents users from fully accessing their systems. Once the malware is released, users are urged to pay a designated ransom to regain access to their systems and data in a timely manner. Without adequate back-ups, many health systems find themselves out of service following a severe ransomware attack, which can materially impact patient care.
Without adequate back-ups, many health systems find themselves out of service following a severe ransomware attack, which can materially impact patient care.
Without access to critical therapy and treatment data, an entire healthcare organization can quickly find its operations disrupted or even halted entirely. In October 2019, a hospital system in Alabama6 found its connected platforms debilitated by a successful ransomware onslaught that forced practitioners to turn patients away at three of its locations, treating only the most critical cases during this period of operational upheaval.
As a result of the breach, the health system had to shift to a manual operations mode. Practitioners resorted to tracking care information and patient data using paper copies. Unable to rely on its systems, the organization eventually acceded to cybercriminal demands and paid a ransom to restore its digital platforms. While hospital officials didn’t disclose the ransom amount paid, facility executives acknowledged that the organization did purchase a decryption key from cyber attackers to accelerate system restoration and gain full access to sensitive patient information. In addition to the impact on patient care, this event made national news, negatively impacting the reputation of the organization. In all, the cost of the attack is likely measured in the millions.
The recent wave of ransomware attacks has even influenced how the U.S. government handles this type of data breach. For years, the FBI advocated that healthcare executives maintain a zero-tolerance policy for paying hackers to restore their online files, folders, and systems. As ransomware and other malware attacks continue to gain momentum and impact, the federal government is reevaluating its viewpoint.
Make no mistake: the FBI still recommends organizations in any industry never pay the ransom demand. The government asserts that paying a ransom after email phishing or some other type of malware attack will only encourage future hackers to perpetrate similar actions online. Worse yet, even after paying the ransom, a company may still not regain access to its digital ecosystems.
However…
The FBI recently published an updated version of the protocol7 for companies navigating a malware event. In the newly posted document, the FBI does recognize that much like the health system in Alabama, when businesses cannot properly function after a cybersecurity lapse, executives should carefully consider all options to safeguard their systems as well as their staff and consumers.
The government asserts that paying a ransom after email phishing or some other type of malware attack will only encourage future hackers to perpetrate similar actions online.
The recent policy changes add an additional layer to the already exceptionally gray and uncertain landscape of cybersecurity. What isn’t uncertain? Ransomware, at least in the near future, isn’t going anywhere and will likely continue to target healthcare organizations using a myriad of channels. Malware is no longer transferred just through email; it is seen on mobile devices and social media because they are being allowed on enterprise networks. As a result, healthcare organizations must always remain vigilant about their cybersecurity practices to keep their platforms well-protected.
HHS recently released proposed modifications designed to significantly update and modernize both the Anti-Kickback Statute (AKS) and the Physician Self-Referral Law (commonly known as “Stark Law”). First enacted in 1989, the Stark Law refers to a set of U.S. federal laws that expressly prohibit the practice of physician self-referral for financial gain. More specifically, it explicitly prevents practitioners from referring Medicare or Medicaid patients to designated health services (DHS) that have an existing financial relationship with the referring physician or the referring physician’s family members.
Though mostly untouched over the last four decades, the Stark Law is now gaining substantial attention from clinicians, patients, and U.S. government officials due to the country’s evolving healthcare system. In 1989, U.S. healthcare was primarily charged on a fee-for-service basis. As a result, the federal government recognized that self-interest and financial gain might influence a physician’s referral decision.
While there have always been statutory and regulatory exceptions, today the Stark Law ultimately mandates that in order to prevent profit motive taking precedence over patient care, physicians are not permitted to make referrals for Medicaid patients to a medical entity with which they have an existing financial relationship. Additionally, the Stark Law prohibits a conflicting entity from filing payment claims with Medicare for services rendered that violate the Stark Law. In fact, the U.S. government stipulates that Medicare cannot legally pay requests submitted from these practices.
The proposed rules support the value- based care initiative by eliminating existing legal barriers that may currently hinder providers from working collaboratively in the best interest of patients, specifically concerning digital environments and collective network security efforts.
The legislators who devised the fraud rules of the Stark Law did so to safeguard patients navigating a fee-for- service healthcare system. However, policymakers have realized that the existing protocol of the Stark Law does not always align with value-based care practices that strive to promote quality, not necessarily volume, throughout the treatment process.
The new safe harbor proposal recognizes that the digitization and connectivity of the U.S. healthcare delivery system required for interoperability and collaboration within a value-based care program also elevates the threat of cyberattacks across the entire healthcare landscape. As practices increase data sharing across multiple systems and sources, a single compromised environment could cause a data breach that shuts down an entire digital ecosystem. As a result of interoperability, a well-orchestrated attack could materially impact the delivery of care within a community.
The proposed Stark Law changes would allow providers to accept technology-related donations that are essential to reducing the risk of a data breach or cyberattack. However, the current proposal outlines limits on what can be donated. For example, hardware is not considered a compliant donation, but the rule does allow network security training services, software, business continuity and data recovery services, practices associated with security risk assessments, threat-sharing services, and cybersecurity-as-a-service offerings.
The proposed updates for physician self-referral laws are currently under review. The proposal is open for comments from impacted providers until December 31, 2019. After commentary has closed, Congress will review the input to determine if anything in the changes warrants a modification. From there, they will vote to decide if these new rules will become permanent legislation.
By expanding opportunities for a safe digital environment, the new Stark Law proposals may also directly impact patient payments.
Cyberattacks cost the average healthcare organization approximately $1.4 million in recovery fees and lost productivity.8
Additionally, administrative costs and data loss prevention initiatives cost the U.S. healthcare system hundreds of billions of dollars annually. Allowing providers to receive donated cybersecurity resources can prove a critical step toward lowering the cost burden for patients across every phase of the care continuum. As health systems evaluate third-party risk these potential changes to the Stark Law could materially impact your strategy.
5Source: https://www.beckershospitalreview.com/cybersecurity/ why-ransomware-other-cyberattacks-have-been-on-the-rise-inside-hospitals-and-how-to-prevent-them
6Source: https://www.healthcareitnews.com/news/alabama-hospital-system-dch-pays-restore-systems-after-ransomware-attack
77Source: https://www.ic3.gov/media/2019/191002.aspx
8Source: https://healthitsecurity.com/news/healthcare-cyberattacks-cost-1.4-million-on-average-in-recovery
Increased Investment in Connected Medical Device & IOT Security: Health systems will invest more heavily in medical device security by leveraging new technologies and strengthening governance programs between IT, security, and clinical engineering.
So how did we do? With the advancement in technology options, many healthcare organizations began the selection process to procure medical device and IoT security technology in 2019. The primary use case was to gain better visibility into medical device security issues by first identifying all the assets on the network and then monitoring their behavior over time. Many organizations made decisions on which technology to procure, and many organizations find themselves in the middle of proof-of- concept development. Most are still determining how to appropriately operationalize these technologies to extract the maximum value.
So how did we do? Cryptojacking is the process of stealing computing resources to generate cryptocurrency (i.e., cryptomining). According to the 2019 SonicWall Cyber Threat Report mid-year update<sup>9</sup>, the volume of cryptojacking hit 52.7 million registered attacks in the first six months of 2019, with over 33 million of those resulting from Coinhive use. This is a 9% overall increase from the last six months of 2018. The larger trend is difficult to assess in part due to the extreme volatility of cryptocurrency prices during 2019 and the shuttering of Coinhive in March, which was widely used by malware groups to cryptojack computing resources. Organizations need to continue to monitor resource utilization on critical assets where this type of malware may bring on an availability impact, as new players and additional cryptocurrencies are introduced.
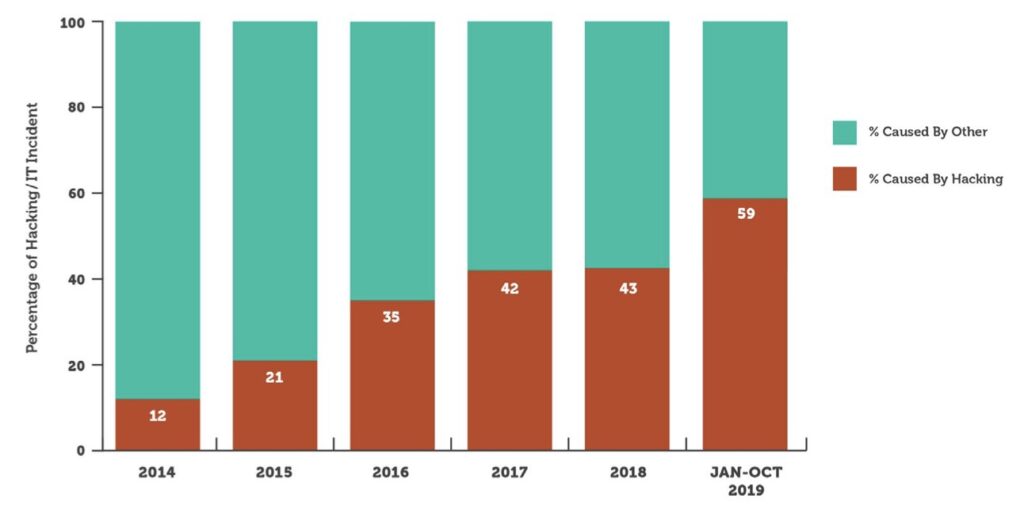
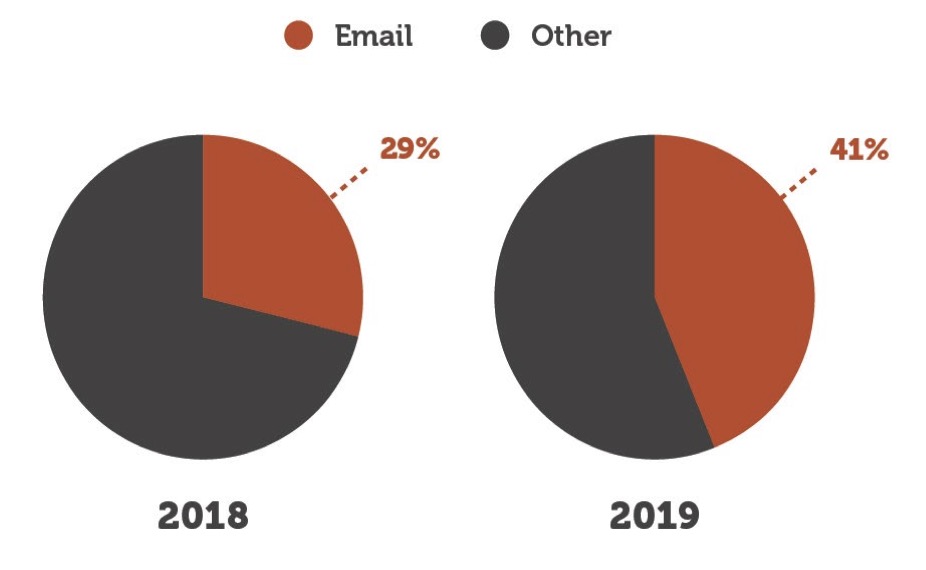
So how did we do? According to the reported OCR breach data1, 41% of successful attacks involved email. This is up from 33% in 2018, representing the sixth consecutive year of increases. Individuals who have access to email on your network remain one of your biggest threats. Organizations should continue to invest in security awareness training and conduct regular simulated phishing exercises.
1Source: U.S. Department of Health and Human Services Office for Civil Rights
9Source: https://www.sonicwall.com/resources/white-papers/mid-year-update-2019-sonicwall-cyber-threat-report/
Cybersecurity Outlook 2020
1
2
3
4
When speaking with healthcare organizations throughout 2018, three major topics consistently came up in almost every discussion:

As our adversaries continue to utilize email as their weapon of choice, it is critical that every healthcare organization develop and implement a simulated phishing program. Be sure to consider culture and human resource requirements to make this program most effective.

It is difficult for some organizations to effectively manage third-party risk due to technology sprawl and the ever-expanding vendor network; however, establishing strong governance and a risk-based model is imperative to protect your organization.

Healthcare organizations often look to technology alone to solve their cybersecurity problems. As a result, they purchase technical point solutions without adequately planning for the ongoing management of these tools, leading to the misconception that their organization is more protected than it actually is. Don’t forget the real value of these tools lies in how you manage and monitor them over time.

Healthcare organizations will make additional investments in endpoint security technologies to secure the threat landscape at the edge. Remember to consider how your organization will operationalize this technology to extract the most value and maximize protection.

Chief Executive Officer
Dan L. Dodson serves as CEO of Fortified Health Security, a recognized leader in cybersecurity that is 100% focused on serving the healthcare market. Through Dan’s leadership, Fortified partners with healthcare organizations to effectively develop the best path forward for their security program based on their unique needs and challenges. Previously, Dan served as Executive Vice President for Santa Rosa Consulting, a healthcare-focused IT consulting firm, where he led various business units including sales for the organization. He also served as Global Healthcare Strategy Lead for Dell Services (formally Perot Systems), where he was responsible for strategy, business planning and M&A initiatives for the company’s healthcare services business unit. Dan also held positions within other healthcare and insurance organizations including Covenant Health System, The Parker Group and Hooper Holmes. Dan is a thought leader in healthcare cybersecurity and is a featured media source on a variety of topics including security best practices, data privacy strategies, as well as risk management, mitigation and certification. He was elected to the Association for Executives in Healthcare Information Security (AEHIS) Board of Trustees in 2022. In 2018, Dan was recognized as a rising healthcare leader under 40 by Becker’s Hospital Review and regularly speaks at industry-leading events and conferences including CHIME, HIMSS and HIT Summits. He served on the Southern Methodist University Cyber Security Advisory Board. Dan earned an M.B.A. in Health Organization Management and a B.S. in Accounting and Finance from Texas Tech University.

Chief Operating Officer
William Crank serves as Chief Operating Officer for Fortified Health Security where his responsibilities include enhancing the company’s services, delivery model, and security operations center. As a member of the executive committee, William works to streamline operations among the sales, solution architect, account management, and customer success teams in addition to continually enhancing Fortified’s expertise by attracting, training, and retaining top security talent. Prior to his role as COO, William was the chief information security officer (CISO) at MEDHOST, a provider of market-leading enterprise, departmental, and healthcare engagement solutions. He has decades of information technology and security experience that include managing the Information Security Risk Management (ISRM) team at Hospital Corporation of America (HCA), where he led a team of Information Security professionals who managed compliance and information security risk and developed and implemented an operational risk management model. William retired after serving 20+ years from the United States Navy. He currently holds multiple certifications in the areas of Information Security and Information Technology. William has also served as Sponsorship/Programs Director and Vice President of the Middle Tennessee chapter of the Information Systems Security Association (ISSA).