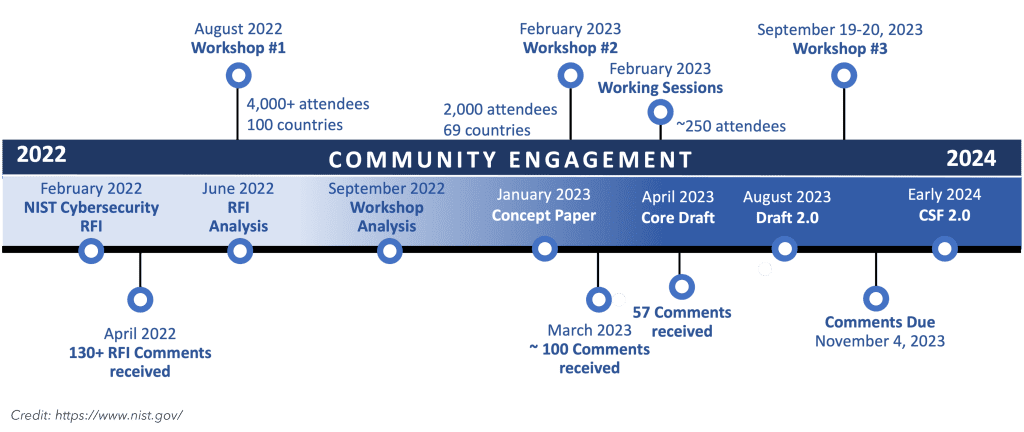
NIST, or the U.S. National Institute of Standards and Technology, is at the forefront of the evolving realm of cybersecurity. Their goal is to provide recommendations that can be used as guideposts for industry best practices and more efficient ways of working
However, cybersecurity is notoriously difficult to build standards around because the threat landscape evolves so rapidly, as does the technology and expertise required to keep up.
In 2014, NIST introduced the NIST Cybersecurity Framework (NIST CSF) 1.0. Tailored primarily for sectors vital to the U.S. like energy and banking, this framework was a beacon of guidance in turbulent cyber seas. Fast forward to 2018, and NIST fine-tuned its Cybersecurity Framework with V1.1, offering clearer terms and strategies to address supply chain risks.
But with cyber adversaries continually advancing their tactics, standing still isn’t an option. Recognizing this, NIST began crafting the next chapter: NIST Cybersecurity Framework 2.0. Slated for a 2024 release, this version is set to address today’s threats while anticipating tomorrow’s challenges.
What to expect with NIST CSF 2.0
1. A new name
NIST CSF version 1.0 was named the “Framework for Improving Critical Infrastructure Cybersecurity,” highlighting its specialized focus. With the advent of 2.0, NIST has opted for a more concise and encompassing title: “Cybersecurity Framework.”
This shift reflects NIST’s aim to be more inclusive of organizations, regardless of their type or size.
2. Improved guidance
NIST CSF 2.0 will provide better clarity around implementing the framework, such as examples of action-oriented processes for each function’s subcategories to help organizations use the framework effectively.
Users will also have access to framework profiles and templates that help them better align their strategy with sector trends, industry best practices, and risk management priorities.
3. More pillars
Up to this point, the CSF has outlined the foundational elements of a robust cybersecurity program through five core functions: identify, protect, detect, respond, and recover. 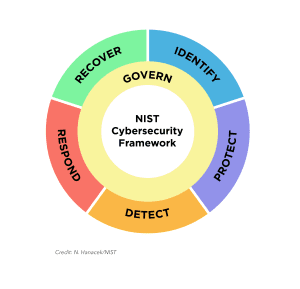
NIST CSF 2.0 introduces a distinct “Govern” function that will guide how an organization can make and execute internal decisions around cybersecurity.
While governance was previously nested under the “Identify” function in Version 1.0, elevating “Govern” as its own pillar underscores its pivotal role. It emphasizes that cybersecurity governance isn’t just an aspect—it’s central to a comprehensive risk management approach and should intertwine with all other NIST CSF categories to achieve the best outcome.
4. Emphasis on supply chain risk management
Within the new “Govern” category, there will be a focus on cybersecurity supply chain risk management. This guidance will reflect the latest NIST framework practices around managing the risks created by doing business with external parties, a concept also referred to as Third-Party Risk Management (TPRM).
5. Clarity on cybersecurity measurement and assessment
Given NIST’s commitment to precision and measurement, the institute wants to refine how organizations communicate and gauge their cybersecurity accomplishments.
NIST CSF 2.0 introduces enhanced details on cybersecurity assessments, supplemented with tiers emphasizing governance, risk management, and third-party considerations. Moreover, the framework champions continuous growth via a fresh “Improvement” category within the “Identify” function. Additionally, users can expect more streamlined guidance on developing profiles and action plans.
What will NIST CSF updates mean for organizations?
NIST CSF 2.0 presents opportunities and challenges for current users and those unfamiliar with the previous framework.
Though adoption to NIST CSF remains optional, bypassing alignment could expose organizations to cybersecurity gaps and escalating risks, especially in sectors like healthcare that are reliant on connected medical devices.
The introduction of the “Govern” pillar is also expected to shift IT leaders’ perspectives on cybersecurity. Limited budgets often relegate cybersecurity to the background; however, the prioritization of governance will likely lead to a renewed emphasis on cybersecurity assessments and strategy planning.
Moreover, while many businesses operate in good faith that their vendors have strong cybersecurity measures in place, this trust can be misplaced, leaving them susceptible to cyber threats. CSF 2.0 aims to enhance third-party risk management education, fostering stronger vendor cybersecurity collaborations. CSF 2.0 is also refining its approach in operational areas, such as moving from basic alerts to ones that integrate with threat intelligence and provide more insight, accuracy, and context.
Even in draft mode, NIST CSF 2.0 foreshadows the potential evolution in how entities manage cybersecurity. When released in 2024, the updated framework will likely have a strong influence on sectors like healthcare. Now is the optimal moment to assess your cybersecurity stance and ensure adequate protection for the future.
Check out our recent webinar to learn more about the evolving landscape of healthcare cybersecurity.


