Alert essentials:
The incorrect implementation of an authentication algorithm in Ivanti Virtual Traffic Manager (vTM) other than versions 22.2R1 or 22.7R2 allows a remote unauthenticated attacker to bypass the admin panel’s authentication.
Ivanti urged customers to patch a critical authentication bypass vulnerability impacting vTM appliances that can let attackers create rogue administrator accounts.
The vulnerability is tracked as CVE-2024-7593; this auth bypass vulnerability is due to an incorrect implementation of an authentication algorithm that allows remote unauthenticated attackers to bypass authentication on Internet-exposed vTM admin panels and the creation of an administrator user.
Detailed threat description:
Ivanti vTM is a software-based application delivery controller (ADC) that provides app-centric traffic management and load balancing for hosting business-critical services.
Ivanti released updates for Ivanti Virtual Traffic Manager (vTM), which addressed a critical vulnerability. Successful exploitation could lead to an authentication bypass and the creation of an administrator user.
Ivanti advises admins to restrict access to the vTM management interface by binding it to an internal network or private IP address to reduce the attack surface and block potential exploitation attempts.
Restricting the exploitability of this vulnerability involves limiting admin access to the management interface through the private/corporate network. Admins must:
- On the VTM server, navigate to System > Security, then click the drop-down for the Management IP Address and Admin Server Port section of the page.
- In the ‘bindip’ drop-down, select the Management Interface IP Address or use the setting directly above the “bindip” setting to restrict access to trusted IP addresses, further limiting who can access the interface.
Affected products / versions:
Expected fix release expectation for supported versions of vTM
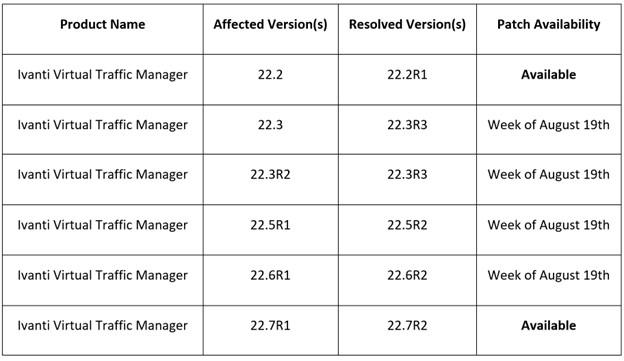
Available patches can be accessed via the standard download portal HERE; a login is required. Patches for all remaining supported versions will be released in the coming weeks.
Recommendations
Actions:
Upgrade to the available patch 22.2R1 (released March 26t26 March 2024) or 22.7R2 (released May 20th20 May 2024).
Customers who have pointed their management interface to a private IP and restricted access can patch as soon as possible.
Fortified recommends applying patches and updates where possible and only after adequate testing in a development environment to ensure stability and compliance with organizational change management policies.
References:


