Alert essentials:
SonicWALL SonicOS management tool features a flaw that could allow attackers to crash the firewall and release ransomware into the network.
Apply version upgrades or workarounds immediately, as this weakness is exploited in the wild.
Detailed threat description:
A critical access control vulnerability is used for access in active ransomware campaigns. Information on the flaw was initially released in August 2024 and was thought to impact SonicOS management access only. No proof of concept was available, nor was an active exploitation observed.
Since disclosure, the weakness has been exploited in the wild, and the scope of the impact has been expanded to include the SSLVPN feature. Most recently, researchers have reportedly seen CVE-2024-40766 used by Akira ransomware.
Firewall generations 5, 6, and 7 are all impacted, and new versions have been released to correct the flaw. Patch or apply the workaround to any affected versions as soon as possible.
This vulnerability has been added to the CISA Known Exploited list, and government agencies have until September 30th to complete patching.
Impacts on healthcare organizations:
Ransomware attacks limit the ability to provide patient care promptly. Medical procedures are delayed, patients’ medical histories are unavailable, and most lifesaving technology is unavailable.
Assume the healthcare organization will one day be a victim of an attack and develop a system to provide patient care with limited or no technology.
Affected products / versions:
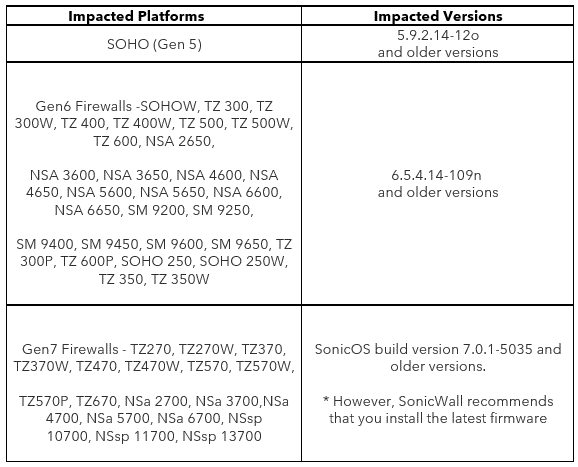
CVE
CVE-2024-40766
Recommendations
Engineering recommendations:
- Apply the patch as soon as possible for impacted products; the latest patch builds are available for download on www.mysonicwall.com
- Or apply SonicWall workaround:
- We recommend restricting firewall management to trusted sources or disabling firewall WAN management from Internet access to minimize the potential impact
- Similarly, for SSLVPN, please ensure that access is limited to trusted sources or disable SSLVPN access from the Internet
*SonicWall strongly advises that customers using GEN5 and GEN6 firewalls with SSLVPN users who have locally managed accounts immediately update their passwords to enhance security and prevent unauthorized access.
- Administrators can force users to change their password by enabling the “User must change password” option in each local account to ensure this critical security measure.
Leadership/ Program recommendations:
- SonicWall recommends enabling MFA (TOTP or Email-based OTP) for all SSLVPN users..
Fortified recommends applying patches and updates where possible and only after adequate testing in a development environment to ensure stability and compliance with organizational change management policies.
References:
- SonicWall Advisory and workaround: https://psirt.global.sonicwall.com/vuln-detail/SNWLID-2024-0015
- https://www.mysonicwall.com/muir/login
- https://arcticwolf.com/resources/blog/arctic-wolf-observes-akira-ransomware-campaign-targeting-sonicwall-sslvpn-accounts/
- CISA KEV: https://www.cisa.gov/known-exploited-vulnerabilities-catalog


