Alert essentials:
Patched SQL Injection vulnerabilities and PowerShell scripts allow hackers to retrieve encrypted passwords without authentication in Progress WhatsUp Gold. Apply the version update immediately and check for compromise.
Detailed threat description:
WhatsUp Gold is an application that monitors Windows networks and IT infrastructure. The software provides complete visibility into the status and performance of applications, network devices, and servers in the cloud or on-premises.
An unauthenticated attacker could exploit vulnerabilities to execute arbitrary code on the WhatsUp Gold instances. Complete system compromise, data theft, and unauthorized access to sensitive information is possible.
On August 16th, a security update was released to update WhatsUp Gold beyond a remote code execution (RCE) vulnerability found in versions under 24.0.0.
The security researcher who discovered the flaws reported it to the Zero Day Initiative on May 22nd. Then, on August 30th, during the Labor Day holiday weekend in the United States, he published a PoC. The release contained instructions for bypassing authentication to get to the RCE and payload deployment phase. Active exploitation was underway roughly five hours after publication.
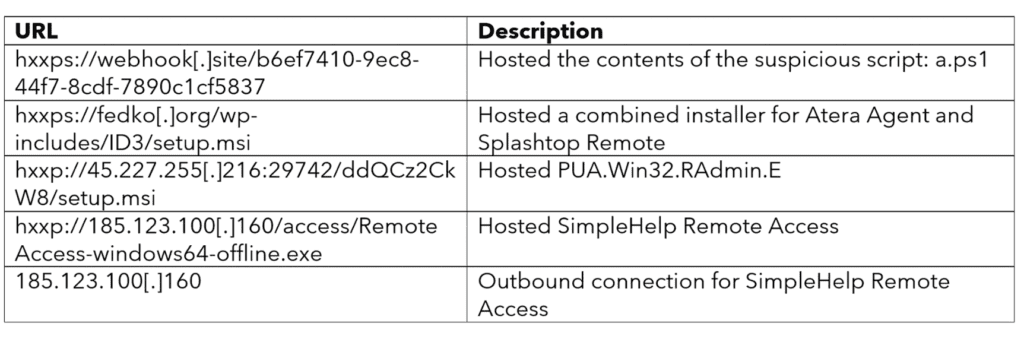
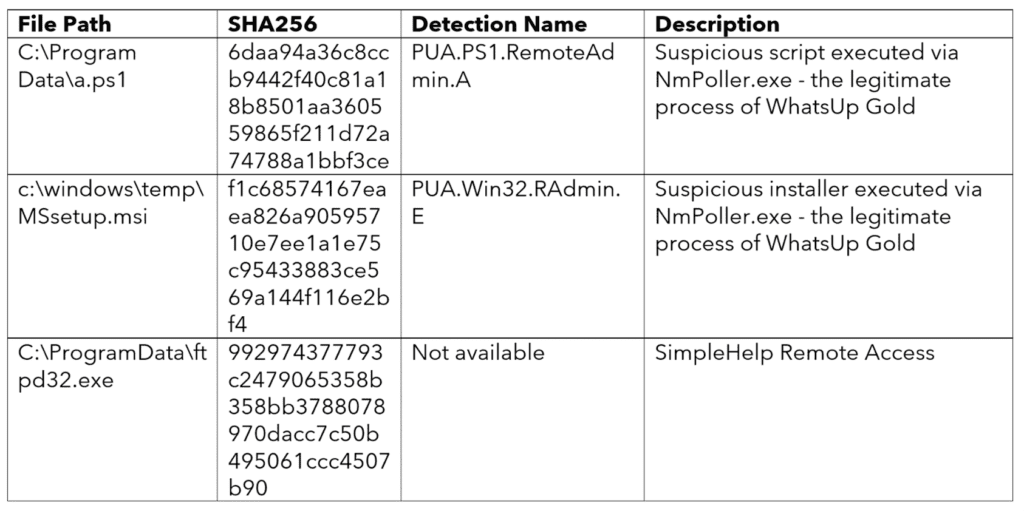
Threat actors exploit the WhatsUp Golds NMPoller.exe to host and run PowerShell scripts. Malicious, arbitrary code allowing the download of remote payloads and installation of suspicious MSIs is then injected into the polling process.
If the application is configured with only one user, a SQL Injection vulnerability allows an unauthenticated attacker to retrieve the user’s encrypted password, resulting in system compromise.
Take note that monitoring the nmpoller.exe process for suspicious process creation events can help detect potential attacks.
Several PoCs have been published on GitHub, and Censys reports have found over 1,200 exposed devices online.
Progress strongly encourages customers on any version older than 24.0.0 to upgrade. All customers with an active service agreement are eligible to upgrade to the latest version free of charge.
Impacts on healthcare organizations:
The increasing number of attacks targeting healthcare organizations emphasizes the valuable nature of patient information data and the need for robust security measures in healthcare networks. Successfully exploited, this unauthenticated attack could render lifesaving technology unavailable for an undetermined time.
Affected products / versions:
CVEs
CVE-2024-6670
CVE-2024-6671
Recommendations
Engineering recommendations:
- Downloading and upgrading to the latest WhatsUp Gold release is possible if the current serial number has an active service agreement
- A direct upgrade is possible for versions 20.0.2 and newer
- Review system requirements before upgrading
- As part of the upgrade to WhatsUp Gold, the SQL Server Express database, which includes WhatsUp Gold, will be updated to SQL Server 2022 Express
- If you use a remote SQL database instead of the default install as part of the default WhatsUp Gold installation, refer to the WhatsUp Gold Database Migration and Management Guide for information about other WhatsUp Gold database configurations
- If you use Scalability Pollers in your environment, they will also need to be upgraded to match the build number
- If Agents were deployed and in use before upgrading WhatsUp Gold, they must be redeployed to apply any available fixes or updated functionality
- To redeploy agents and fully complete your upgrade of WhatsUp Gold, ensure you are logged in to WhatsUp Gold using an admin account with permissions to deploy WhatsUp Gold Agents.
- Next, navigate to SETTINGS > WhatsUp Gold Agent > Agent Library from the main menu. Select all existing agents displayed in the library, then click Deploy Agent
- This process updates agents in batches of five
- If you have a large quantity deployed, this process can take several minutes to complete
- Tighten access controls on WhatsUp Gold and all other applications
- Monitor PowerShell scripts through SIEM or by developing a PowerShell performance monitoring script
- By monitoring for unexpected events like product restarts, logfile creations, and spikes in event frequency, administrators can identify malicious activities such as external MSI package installations, RAT installations, and suspicious file creations
- Download and install the MySQL .NET Connector on the WhatsUp Gold machine to monitor a MySQL database
Leadership/ Program recommendations:
- Install MFA in the environment
- Use passkeys instead of passwords if possible
Fortified recommends applying patches and updates where possible and only after adequate testing in a development environment to ensure stability and compliance with organizational change management policies.
References:
- Progress Security Bulletin: https://community.progress.com/s/article/WhatsUp-Gold-Security-Bulletin-August-2024
- MySQL .NET Connector: https://dev.mysql.com/downloads/connector/net
- Passkeys: https://passkey.org/
- PowerShell Monitoring: https://www.techtarget.com/searchitoperations/tutorial/Build-a-PowerShell-performance-monitoring-script-step-by-step
- Progress WhatsUp Gold 24.0.0 Release Notes with KNOWN ISSUES: https://docs.progress.com/bundle/whatsupgold-release-notes-24-0/page/WhatsUp-Gold-2024.0-Release-Notes.html?_gl=1*1dtp39i*_gcl_au*MTE0NDkyMTAyNS4xNzI2NjczOTEx*_ga*MTkxMTM2MDg2Ni4xNzI2NjczOTEx*_ga_9JSNBCSF54*MTcyNjc0ODM5NC4yLjAuMTcyNjc0ODQ0MS4xMy4wLjA.#System-Requirements
- Progress Upgrade Requirements: https://docs.progress.com/bundle/whatsupgold-release-notes-24-0/page/WhatsUp-Gold-2024.0-Release-Notes.html?_gl=1*1dtp39i*_gcl_au*MTE0NDkyMTAyNS4xNzI2NjczOTEx*_ga*MTkxMTM2MDg2Ni4xNzI2NjczOTEx*_ga_9JSNBCSF54*MTcyNjc0ODM5NC4yLjAuMTcyNjc0ODQ0MS4xMy4wLjA.#System-Requirements
- TrendMicro Technical Details of Exploit: https://www.trendmicro.com/en_us/research/24/i/whatsup-gold-rce.html