Alert essentials:
The GhostSpider backdoor is a sophisticated tool used in ongoing cyber espionage campaigns attributed to Salt Typhoon.
Its advanced capabilities include operating entirely in memory, encrypted communications with command-and-control (C2) servers, modular data exfiltration, and system tampering functionality.
Be sure all systems are on the latest software version and have received the latest security patches.
Detailed threat description:
Salt Typhoon, or GhostEmperor, is a Chinese-speaking threat actor that targets government entities and telecom companies. Originally zeroing in on Southeast Asian organizations, the threat actor uses a Windows kernel-mode rootkit called Demodex and a cross-platform backdoor to gain remote control over their targeted servers.
Also known as UNC4841 or Earth Estries, their nefarious activities came to light in May of 2023 with the successful exploitation of CVE-2023-7101 on Barracuda security gateways.
Demonstrating high sophistication, the bad actor uses a wide range of malware and purpose-built tooling along with anti-forensic and anti-analysis techniques to enable and conceal operations.
Their work has been observed in at least twenty-six verticals, including healthcare and biotechnology, public health, telecoms, and semiconductors. Victims have been identified in over a dozen countries like Afghanistan, Brazil, Eswatini, India, Indonesia, Malaysia, Pakistan, the Philippines, South Africa, Taiwan, Thailand, the U.S., and Vietnam.
Their most recent espionage activities focus on organizations in the U.S., Asia-Pacific territory, the Middle East, and South Africa.
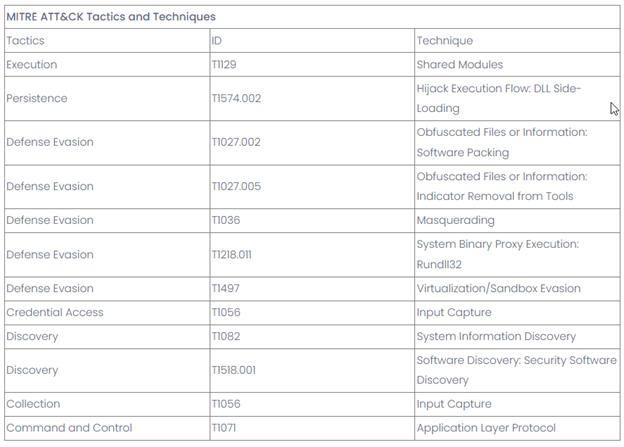
Last week, researchers observed a resurgence in the GhostSpider backdoor in Salt Typhoon’s ongoing campaigns. The tool is deployed using known vulnerabilities in software like Ivanti VPN, Fortinet, Sophos Firewall, and Microsoft Exchange.
It uses encrypted communications and custom protocols to evade detection and maintain secure communication with C&C servers. The highly adaptable backdoor operates entirely in memory and uses various modules to suit different espionage objectives.
After entering the network, the bad actor employs living-off-the-land binaries for lateral movement and deploys malware to ensure persistence and extensive network infiltration.
The group’s long-term objective appears to be the strategic infiltration of critical infrastructure, refining attack methods, and penetrating multiple levels of organizations, including secondary contractors and service providers.
This campaign and similar persistent risks can be mitigated with a proactive security posture and collaboration with cybersecurity experts.
Impacts on healthcare organizations:
The impact of an exploit like GhostSpider underscores the need for robust cybersecurity practices, as cyberattacks can cripple healthcare operations, delay treatments, and disrupt services.
Healthcare organizations are attractive targets for cybercriminals seeking valuable intellectual property related to pharmaceuticals, treatments, or medical technologies.
Organizations should invest heavily in advanced cybersecurity solutions, staff training, and real-time threat detection to counteract operational downtime from network intrusions.
Affected Products / Versions:
CVEs
- Ivanti Connect Secure VPN (CVE-2023-46805, CVE-2024-21887): Exploited for arbitrary command execution
- Fortinet FortiClient EMS (CVE-2023-48788): SQL injection vulnerability
- Sophos Firewall (CVE-2022-3236): Code injection allowing remote code execution
- Microsoft Exchange (ProxyLogon CVE-2021 series): Remote code execution vulnerabilities
Recommendations
Engineering recommendations:
- Update all applications/software regularly with the latest versions and security patches
- Ensure that your vulnerability management process includes timely and effective remediation of high-severity vulnerabilities, especially those affecting externally facing services
- Implement competent security protocols and encryption, authentication, or access credentials configurations to access critical systems in your cloud and local environments
- Ensure that backups of critical systems are maintained, which can be used to restore data in case a need arises
- Network segmentation limits the impact of an intrusion
- Enhance Network Traffic Analysis for Command-and-Control (C&C) Communication
- Build and undertake safeguarding measures by monitoring/ blocking the IOCs and strengthening defense based on the tactical intelligence provided
- Employ behavioral analytics to detect abnormal system behavior, such as sudden spikes in encrypted outbound traffic or unusual memory usage
Leadership/ Program recommendations:
- Strengthen Vulnerability Management and Patch Management Programs
- Enable zero-trust architecture and multifactor authentication (MFA) to mitigate the compromise of credentials
- Conducting regular red team exercises will help simulate real-world attacks, providing valuable insight into how attackers might exploit weaknesses in your environment
- Ensure that your team has access to advanced malware analysis tools to reverse-engineer new variants and develop custom signatures for effective detection
- Use robust endpoint detection and response (EDR) solutions to identify in-memory threats and lateral movement tactics
- Develop and test incident response plans, including strategies for memory analysis and rapid threat containment, as GhostSpider remains in memory to evade detection
- Enforce policies to validate third-party software before installation
- Educate employees about phishing and social engineering attacks, which often serve as initial vectors for deploying backdoors like GhostSpider
Fortified recommends applying patches and updates where possible and only after adequate testing in a development environment to ensure stability and compliance with organizational change management policies.
References: