Every single facility that treats patients and gathers patient data is a target for a cyberattack, and this risk is growing.
In just the first six months of 2023, more than 300 data breaches were reported to the U.S. Department of Health and Human Services Office of Civil Rights (OCR), an increase of more than 104% compared to mid-year 2022. Those breaches affected over 40 million patient records, a year-over-year increase of 60%.
What are these cybersecurity threats? And how can hospitals and health systems protect themselves?
This post focuses on six cybersecurity threats, and what hospitals can do to defend their organizations against threat actors.
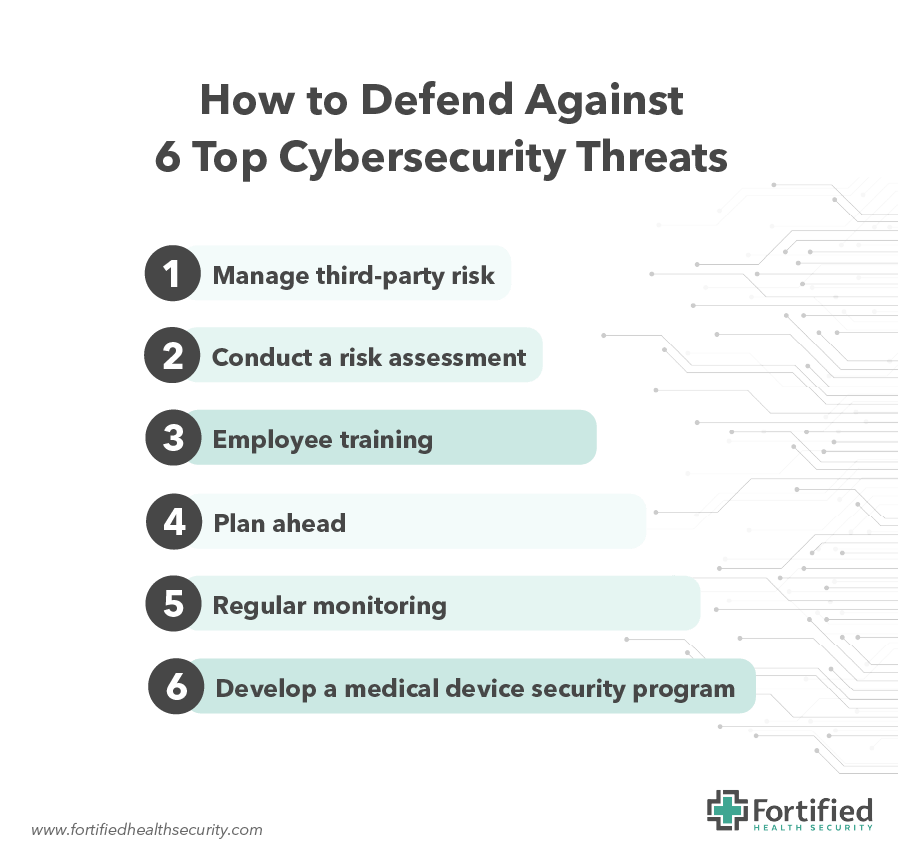
6 top cybersecurity threats and how to defend against them
1. Third-parties
Hackers love to exploit the weakest link in the security chain. Hospitals maintain hundreds of APIs and other connections between healthcare and non-healthcare organizations, and every one of those third-party connections is vulnerable.
Increasingly, technology is supplied as Software-as-a-Service (SaaS) because it offers frequent software updates and always-on capabilities. SaaS tools have their advantages, but hospitals and health systems rely on the security of the network connection between a vendor’s network and their own IT network.
Hospitals are also trusting the SaaS provider to protect the patient data they store on behalf of hospitals. This is problematic, as it may decrease the visibility and control hospitals have over the security of their data. To bring this point home, between mid-year 2022 and 2023, breaches caused by business associates skyrocketed by 273%.
What you can do: Manage third-party risk
By implementing a third-party risk management program (TPRM), you’ll be better equipped to identify third-party business associates that might be introducing risk into your environment. Any new technology solution you introduce into your organization should have a risk assessment conducted as part of the selection process – before a contract is signed. Technology changes rapidly in every organization, so assessing their potential risk to your organization on an ongoing basis is vital.
2. Ransomware attacks
Ransomware is a type of malware that infects a computer system and encrypts files, making them inaccessible to the company. Cybercriminals then demand payment in exchange for a decryption key to restore access to the files. However, those files often aren’t returned and another ransom is demanded.
Federal authorities caution against paying the ransom, but many hospitals do so anyway because of the 24/7 nature of healthcare and the core mission of caring for patients. Ransomware attacks have become increasingly common in healthcare, and they can cause significant financial and reputational damage, as well as disrupt patient care.
What you can do: Conduct a risk assessment
Risk assessments are critical to understanding the cybersecurity posture of your organization. They help you better understand the threats and vulnerabilities that could impact your health system and provide guidance on the best strategies and tools to mitigate those risks.
3. Phishing attacks
More than 90% of cyberattacks start with a phishing incident, and the numbers keep rising. Attacks spiked 87% across industries last year, including a 356% surge in advanced phishing attacks.
Phishing attacks are used to trick people into divulging sensitive information such as login credentials, credit card numbers, or personal data. Once they gain access to a system, bad actors can pivot to more sensitive areas, including patient records or financial data. These attacks can be particularly effective in healthcare environments because employees are juggling multiple patients or moving between care settings and may be more likely to click on a link or open an attachment without fully considering the consequences.
What you can do: Employee training
The best Security Awareness Training (SAT) programs use engaging, personalized storytelling, and memorable content to change human behavior and help people retain information. Content delivered in short segments (e.g., a monthly 5-7 minute video) is preferable to 30—60 programs delivered infrequently.
4. Data breaches
A successful cyberattack that affects more than 500 patient records must be reported to the Office of Civil Rights (OCR) before it’s officially labeled a “breach.”
The OCR maintains a so-called “Wall of Shame” of offending healthcare providers, payers, clearinghouses, and business associates. In addition to the costs directly associated with any leveraged fines and remediating the effects of any breach, hospitals face a loss of reputation in the communities they serve and a potential loss of patient loyalty.
During the first six months of 2023, 75% of reportable breaches were attributed to hacking, and 21% were from unauthorized access or disclosure, which is on the rise. Network servers account for two-thirds of breaches, while another 20% start with a malicious email.
What you can do: Plan ahead
Unfortunately, it’s not a question of whether your hospital will be impacted by a phishing attack, ransomware demand, or data breach — it’s a question of when. The planning you do today will benefit your hospital when the inevitable occurs. Understanding how networks are connected, determining your hospital’s vulnerabilities, creating an incident response plan, and testing that plan can help reduce the sting when an actual attack occurs.
5. Legacy systems
Hackers exploit vulnerabilities in older software that may no longer be in production but is needed for historic search capabilities due to regulatory requirements, or it is just too expensive to replace. There may be hundreds of these legacy systems within a hospital’s technology stack, and these outdated technologies may not have the latest patches, leaving the door open for threat actors to exploit these forgotten legacy systems and gain access to critical hospital data.
What you can do: Regular monitoring
Continuous oversight of your legacy systems can reduce the likelihood of an attack. But an important reality to acknowledge is that keeping up that vigilance often competes with other IT department priorities. These may include new technology projects, strategic long-term planning, and managing the routine activities essential for the smooth operation of contemporary technology infrastructure. Remember that security is never a one-and-done proposition. Scanning and patching should be ingrained in IT staff.
Many hospitals outsource this function to a managed security service provider who can monitor client networks 24/7/365. For example, Fort HealthCare in Wisconsin saw a 50%+ reduction in critical and high vulnerabilities within six months of an outsourcing engagement.
6. Medical devices
Medical devices are another area where hospitals often come up short in terms of cybersecurity and they can no longer be ignored. Internet of Medical Things (IoMT) devices transmit patient data to employee health records, but they can be notoriously difficult to track and patch, much like legacy software. Non-functioning medical devices during a cyberattack have been the subject of lawsuits where patients were affected.
What you can do: Develop a Medical Device Security Program.
While this may feel like a daunting task, it is achievable if you break it down based on risk and achievable outcomes (i.e., “quick wins.”). Focus on what your hospital can do, versus what it can’t do. If capital is unavailable to replace a $100K imaging machine, turn to devices that have the same risk score but that need a minor software update or patch to reduce risk.
Keys to cybersecurity success: People, processes, and technology
While there are many ways a hospital can tackle the top cybersecurity threats facing the industry, success requires a combination of people, processes, and technology.
A successful cybersecurity program requires a balance among all three components.
Technology alone is not enough to protect against cyber threats. Processes must be in place to ensure that technology is being used effectively and that employees are trained and equipped to follow those processes. In the same vein, processes alone are not enough. They must be supported by effective technology that can detect and respond to potential and emerging cybersecurity threats.
The best defense against increasingly sophisticated cyberattacks is to ensure your organization is meeting — or working towards meeting — the guidance and best practices outlined by the Health Sector Coordinating Council, which are developed in collaboration with organizations across the healthcare ecosystem to foster a proactive approach to cyber threats.
Learn more on our on-demand webinar, The Regulatory Roadmap with HSCC.


