On April 16th, healthcare industry leaders gathered in Washington, DC to testify to the Energy and Commerce Health Subcommittee on the topic of “Examining Health Sector Cybersecurity in the Wake of the Change Healthcare Attack.”
The insights these leaders shared around the sector-wide risks facing healthcare and the potential steps forward to address them were timely and enlightening. While Change Healthcare was the focal point of this discussion, there were many areas of concern that were brought up during the hearing, including:
Vertical consolidation
The industry experts testified to concerns around the growing vertical consolidation in healthcare as well as the impact that future merger and acquisition requests could have on cybersecurity risks to the healthcare sector.
The attempted block of the Change Healthcare acquisition by United Health Group (UHG) in 2022 by the Department of Justice was mentioned in this context. Congress was asked to consider evaluating cybersecurity risk when reviewing future mergers and acquisitions and fully understand any risk this might pose to the health sector.
In addition, a few key facts were shared about UHG’s size and scope, including:
- Currently 90,000 doctors are employed by UHG, representing nearly 10% of all US physicians
- Over 15 billion healthcare claims are processed annually through Change Healthcare’s clearinghouse, representing 1 out of every 3 claims
- The perception that UHG capitalized on the Change Healthcare incident by obtaining emergency approval to acquire a healthcare organization in Oregon that had suffered from this attack, allowing them to further expand their reach
Concerns were also raised about the potential for organizations of this size and reach to introduce low-redundancy, high-impact risks to the sector.
Recovery time
The prolonged recovery from this incident has placed significant financial strains on healthcare organizations. Members of Congress have repeatedly voiced concerns over the extended duration of UnitedHealth Group’s recovery efforts, now in its eighth week, with many applications still offline.
Due to the confidential nature of the ongoing attack, panelists were unable to directly address this concern as they lacked insight into the UnitedHealth Group network.
Risks to reimbursement
The complexity of the claims process within healthcare has led to countless healthcare organizations struggling to:
- Verify insurance
- Obtain prior authorizations
- Submit claims in a timely fashion
- Implement an alternative clearinghouse
- Address patients’ pharmacy concerns
- Reconcile payments
To adjust to these manual processes, providers have had to pay overtime rates and even hire additional staff, none of which are expected to be compensated by UHG.
Although UHG did make some payment advancements available, these were only a fraction of the usual amounts received by providers. UHG stated that it could not access payer information beyond its own to substantiate these advance payments. Furthermore, UHG required substantial information from providers, raising concerns among many that this data might be used to leverage future acquisitions.
UnitedHealth Group has also agreed to testify, so stay tuned to hear the other side of the story.
Risks to patients
Panelists and Congress members shared numerous stories illustrating the impact of the Change Healthcare cyber incident on patients. These included:
- A Patient forced to pay $1,100 out-of-pocket for essential medication because her payment card was declined at a pharmacy
- Patients unable to receive critical services due to missing prior authorizations or insurance verifications
- Widespread confusion from erroneous billing caused by inaccessible remittance advice documents from UHG
- Diverting healthcare staff from patient care to manual administrative processes
Panelist Scott MacLean, Senior Vice President and Chief Information Officer at MedStar Health and emphasized the severity, stating, “Because patient care is at the heart of each of our members’ core mission, even one member reporting that this incident impacted patient care is unacceptable.”
Hearing healthcare cybersecurity concerns
The panelists and House committee members raised additional concerns around healthcare cybersecurity, including:
Healthcare sector security gaps
While the Health Sector Coordinating Council Cybersecurity Working Group (HSCC CWG) has consistently provided recommendations and guidance on cyber risks to the healthcare industry, HSCC’s Executive Director, Greg Garcia, highlighted ongoing vulnerabilities and numerous uncertainties within the sector during his testimony. He specifically pointed out the challenges in identifying all low-redundancy, high-impact areas within the current healthcare ecosystem.
Growth outpacing investment
The widespread digitization of the healthcare industry has greatly improved patient care, but investments in securing this rapidly expanding digital landscape have significantly lagged. Panel members emphasized this problem, highlighting how the Change Healthcare incident has affected both the financial stability of healthcare organizations and their capacity to provide patient care.
Recommendations for improvement
The panelist offered a diverse set of recommendations to the committee on what the government can do to help prevent incidents like the Change Healthcare breach from recurring.
Adopt and implement CPGs
Although it was strongly recommended that healthcare organizations adopt and implement the Cybersecurity Performance Goals (CPGs) recently outlined by the Department of Health and Human Services (HHS), there was some debate over whether these guidelines should remain voluntary or become mandatory.
Whether they are voluntary or mandatory, there was consensus from the panel that the CPGs are a good basis for improving the overall posture of healthcare cybersecurity.
Ensure secure by design solutions for all vendors
Given the reliance on external organizations to develop and maintain software in the healthcare industry, there was significant discussion on the criticality of third-party vendors within healthcare to ensure their software is “secure by default and secure by design.”
At present, there is wide disparity in the attention given to security during software development, the speed of addressing identified vulnerabilities, and the strategies for mitigating overall risks in the health sector. This inconsistency extends to the diverse array of products used within healthcare facilities.
Rapid response teams
One recommendation posed by Greg Garcia, Executive Director of the Health Sector Coordinating Council (HSCC), was the development of a “rapid response” capability for cyber incidents to enable faster organizational recovery. In his testimony, Garcia proposed what could be termed a “Healthcare Cyber FEMA” or a “911 Cyber Defense.”
He stressed the urgency of the health system’s reliance on immediate response times—minutes and hours, rather than months. Garcia advocated for investing in a rapid response team to counter systemic attacks, using government authority to declare a “national cyber emergency.”
This would activate national cyber insurance to complement private coverage, provide swift financial aid, allow for temporary suspension of certain regulatory constraints, and deploy mobile healthcare services to support those critically affected. This strategy also forms part of HSCC’s proposed Health Industry Cybersecurity Strategic Plan.
Provide cybersecurity funding
The issue of funding for healthcare cybersecurity was a recurring theme throughout the discussions, with particular emphasis on under-resourced organizations that struggle to adequately finance their cybersecurity initiatives. There was a call for a cyber “safety net” for the nation’s most vulnerable healthcare providers.
Perform a health infrastructure mapping and risk assessment
The Change Healthcare incident highlighted a critical dependency within the health sector, revealing an overreliance on key business components. It underscores the urgent need to identify areas of low redundancy that carry high risks and are crucial to healthcare operations, posing significant threats to the national security of the healthcare sector.
Implement Health Industry Cybersecurity Strategic Plan
By following the goals and implementation objectives within HSCC’s recently released five-year strategic plan, risks to healthcare can be greatly reduced.
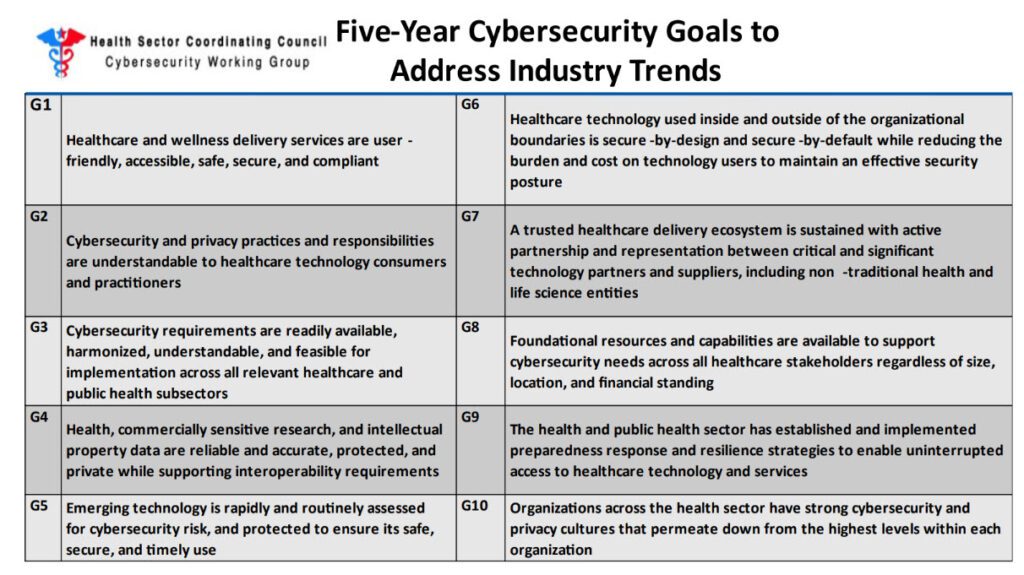

(Image source: Health Sector Coordinating Council Cybersecurity Working Group)
If you were unable to watch the hearing live, you can catch the recording of it or read the written testimony of the panelists on the Energy and Commerce’s website.


