What is attack surface management?
Think of your attack surface as a fortress with multiple entry points. Each entry point represents a system or network weakness that could potentially be breached by an intruder.
These weaknesses, like outdated patches, misconfigurations, and traditional vulnerabilities, serve as open doors or unguarded walls that can be exploited by a threat actor. Effective attack surface management is crucial in reducing these vulnerabilities and fortifying your defenses.
In the healthcare industry, where patient well-being relies on critical medical devices and uninterrupted operation, reducing the attack surface becomes a top priority.
With attack surface management as a fundamental strategy, healthcare organizations can enhance their overall security posture, mitigate potential risks, and prioritize patient safety. By proactively tending to their attack surface, hospitals and health systems can create a resilient digital infrastructure that safeguards both their operations and the well-being of their patients.
What is a VTM program?
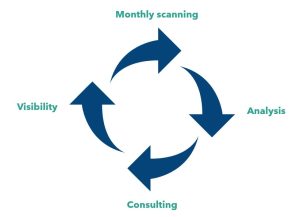
VTM, or Vulnerability Threat Management, serves as a powerful tool for cybersecurity teams in their mission to reduce and manage their attack surface, with the ultimate goal of protecting patients.
At the heart of a VTM program lies routine scanning, ideally conducted on a monthly basis. These scans are essential for identifying, understanding, and quantifying the vulnerabilities present in your attack surface. By analyzing these vulnerabilities and considering how to fix them, you gain valuable insights that help you prioritize which areas to address first and whether additional measures are needed to compensate for the risks. This proactive approach enables you to effectively mitigate potential threats and reduce the overall risk to your systems and networks.
The visibility obtained through the VTM process is vital for making incremental and consistent reductions in your attack surface. After all, you cannot protect what you cannot see.
To maximize the benefits of VTM, it is advisable to acquire it as a service, which should include ongoing consultation to continually inform and enhance your program, aligning it with industry best practices.
Challenges of VTM and attack surface management in healthcare
People
Implementing a self-managed VTM program can be labor intensive. It involves handling several essential tasks, such as setting up the scanner, ensuring regular scheduling of scans, and determining the scope of what needs to be scanned. For IT staff already juggling multiple priorities, this can feel like a significant undertaking.
Moreover, conducting these scans within a healthcare environment introduces inherent risks.
While the need to treat sensitive systems like medical devices (MRI machines, heart monitors, or IV pumps) with utmost care is evident, it’s also crucial to consider the broader picture.
What about the Windows or Unix systems that control an entire wing of these critical medical devices? Ignoring their vulnerabilities could lead to potential failures or breaches.
One way that hospitals and health systems ensure effective attack surface management and execution of their VTM program is by relying on experienced professionals. This allows their IT staff to focus on their core duties while the responsibility of conducting scans is entrusted to professionals who can handle it with precision and expertise.
Processes
Change management programs need to be continuously improved, especially when it comes to vulnerability threat management. However, how one team believes a system should be patched/updated/configured may not align with the view of other teams in the same organization.
The lack of clear processes and procedures to manage these complexities poses a significant challenge for a successful VTM program. Without well-defined guidelines in place, finding the right answers becomes difficult, hindering the program’s effectiveness.
Adding to the challenge is that there’s often a lack of community sharing and awareness around cybersecurity within healthcare organizations. Without clear lines of communication, VTM program managers are unable to maximize the potential of their programs, and healthcare organizations miss out on valuable insights and collective intelligence that could significantly strengthen their overall cybersecurity defenses.
Technology
If you’re new to VTM technology, brace yourself for a steep learning curve. The navigation and various features and functionalities of different VTM products can vary significantly.
Finding the right balance in terms of scanning frequency can also be tricky. Scan too infrequently, and critical vulnerabilities might slip through the cracks. Scan too often, and you might end up encountering the same vulnerabilities repeatedly, wasting valuable time and resources.
If you’re implementing a VTM solution on your own, it’s important to note that you’re also responsible for managing the technology vendor relationship and handling all the necessary check-ins. This additional workload further adds to the people-hours required to successfully implement and maintain your VTM program.
Considering all these complexities, it’s ideal to have at least one dedicated staff member solely focused on managing your VTM program. However, it’s important to recognize that not every organization has the luxury of allocating such resources. Many organizations face budget constraints or staffing limitations, making it challenging to have a dedicated team member solely devoted to VTM management.
Best practices for strong VTM and attack surface management
Despite the challenges, with the proper planning and resources in place, your VTM program can thrive for years to come. Following some industry best practices can help you get there.
1. Find the ideal schedule for your program
Striking the right balance in timing your scans is crucial. With limited human resources, it’s essential to avoid excessive scanning that repeatedly uncovers the same vulnerabilities. On the other hand, it’s equally important to conduct scans frequently enough to uncover vulnerabilities at least once. Finding the sweet spot in scan timing may require some trial and error, so it’s important to factor in this consideration when planning your program.
2. Align and communicate priorities with your teams
In addition, if you have a VTM service provider, open and honest communication is equally crucial. Your provider plays a vital role in offering recommendations, and their insights will be more effective when they have access to all the necessary information. Collaborate closely with your provider, providing them with comprehensive details about your systems, network infrastructure, and any specific concerns or priorities. This enables them to tailor their recommendations to your unique context and align their efforts with your goals.
Ensure that every team, including executive leadership, has a representative attending your VTM scan calls. It’s essential to foster clear communication channels and convey priorities effectively. For example, if your current priority is 3rd party patching, make sure to communicate this clearly to everyone on your team so they understand the need to focus their full attention on that area.
3. Use the right tools for right now
Success with a VTM program and attack surface management requires having the right tools for the job.
Using a vulnerability scanner as a makeshift patch deployment tool, for instance, can lead to ineffective results. Vulnerability scanners and patching tools serve distinct purposes and were developed to perform separate functions.
While vulnerability scanners are designed to identify vulnerabilities, patching tools are specifically created to apply patches and updates. Attempting to use a patch deployment tool to uncover vulnerabilities can yield inaccurate results. And even if a vulnerability is identified, the tool may not provide the necessary guidance for successful patch implementation. The point is that, to maximize their effectiveness in your program, VTM tools should be used according to their intended functions.
Furthermore, in the rapidly evolving cybersecurity landscape, staying in sync with the latest technology and resources is essential for optimizing your VTM program. Your technology partner should demonstrate a commitment to keeping pace with industry trends and emerging threats.
By aligning your tools with their intended purposes and partnering with a technology provider that demonstrates continuous improvement and industry awareness, you can enhance the overall performance and success of your VTM program.
Simplifying cybersecurity solutions
If a service provider manages your VTM program, you should expect them to actively demonstrate innovative thinking, continually improve their service delivery, and provide you with easily accessible program metrics on an ongoing basis.
A unified platform that consolidates all your cybersecurity services into one location is one effective way to ensure that your VTM program remains up-to-date, adaptive, and reliable in addressing the ever-evolving cybersecurity challenges.
As an example, Fortified’s Central Command platform provides a comprehensive view of an organization’s entire cybersecurity program, allowing teams to identify and track risks, actively monitor threats, and respond quickly and effectively to incidents.
For those focusing on the vulnerabilities themselves, this type of platform can enhance the efficiency of their attack surface management by sorting and filtering vulnerabilities by severity, as well as identifying and reducing potential entry points that could be exploited by attackers.
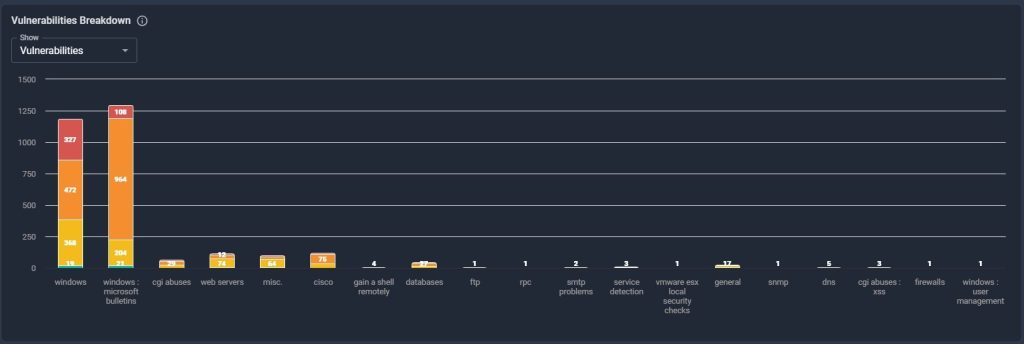
This type of technology can help security teams streamline resources, refine their processes, improve communication across teams, and fortify their systems against potential threats.
Reducing your attack surface and improving your VTM
By embracing the best practices shared here, you can create a robust VTM program, effectively shrinking your attack surface. In turn, you’ll safeguard critical medical devices and achieve your ultimate goal: keeping patients safe.
To learn more about how to best implement VTM in your healthcare environment, check out our on-demand webinar, Attack Surface Management with VTM.