A disheartening reality is that cyberattacks targeting healthcare and other critical industries are on the rise, making it more important than ever for organizations to implement thorough security measures.
This is where single sign-on (SSO) and multi-factor authentication (MFA) come in.
By combining these tools, healthcare organizations can protect themselves while also improving the user experience for employees.
In this post, we’ll dive into the key differences between SSO and MFA and how to set your staff up for success in this ever-evolving threat landscape.
What is single sign-on?
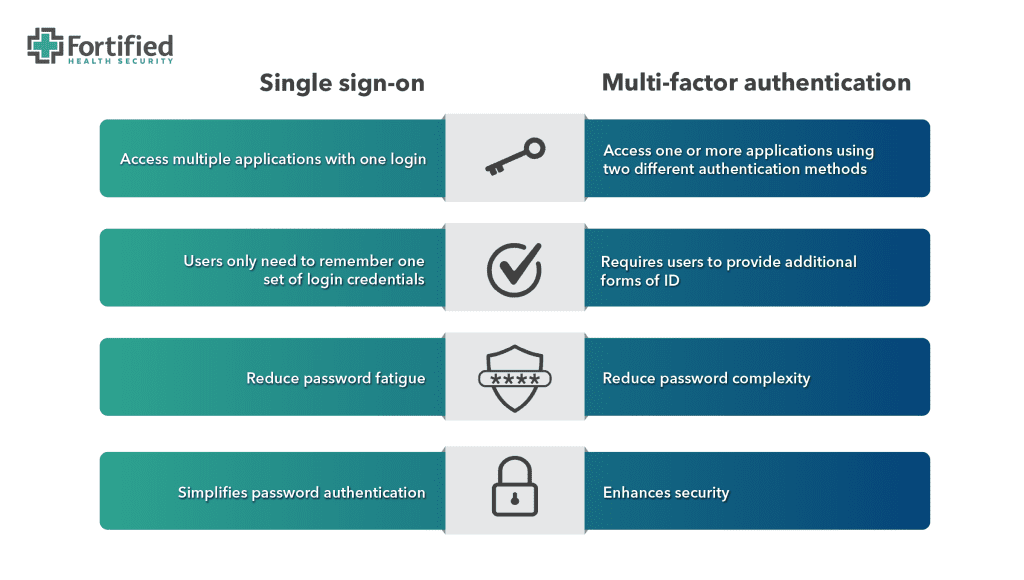
Single sign-on (SSO) is a one-to-many authentication method that allows users to access multiple resources using a single username/password combination.
Depending on the organization and employee’s role, at any given time, medical users may need to access their electronic medical records systems, then toggle over to the laboratory software, pharmacy system, bed management system, and so on.
In healthcare environments, where 24/7 uptime and immediate access to multiple applications is mission critical, SSO can be particularly helpful for ensuring that authorized users can easily and securely access the information they need to provide quality patient care.
SSO benefits
Single sign-on offers several benefits:
Productivity: SSO allows users to access multiple resources efficiently and securely, reducing potential downtime lost to account lockouts or forgotten credentials.
User experience: Accessing applications on multiple devices with one sign-on improves the working experience of your staff.
Compliance: By providing a secure and centralized auditable authentication mechanism, SSO helps organizations comply with their regulatory requirements, such as HIPAA and Payment Card Industry Data Security Standard (PCI-DSS).
Security: SSO has been shown to improve adoption of password complexity and multi-factor authentication among healthcare employees, resulting in improved security.
Monitoring: SSO makes it easier for IT departments to monitor user activity and limit data access through robust account administration and auditing features. This is especially important in industries like healthcare where there may be high turnover and professional contracting.
Potential pitfalls of SSO
No technology is foolproof, and SSO as a user authentication strategy is no exception.
Despite the many positive benefits of SSO, there are some notable pitfalls of SSO, including:
Access: SSO introduces new layers of complexity and potential reliance on 3rd party platforms. This could impact access to applications should a logon portal become inaccessible or malfunction.
Interoperability: Legacy applications that don’t support SSO can pose challenges for IT teams, who may need to create exceptions and workarounds to ensure these applications continue functioning. However, such bypasses can introduce security gaps that remain open for longer than intended, giving a false sense of protection, and potentially making public-facing applications more vulnerable to attack.
Threat detection: Over-reliance on one single authentication mechanism can make it harder for security teams to detect suspicious behaviors as it can be difficult to distinguish between legitimate and unauthorized user activities.
Credential stuffing: SSO can increase exposure to credential stuffing attacks, which is when hackers use compromised sessions or stolen credentials from one application to gain access to another application connected to the same SSO system.
New risks: There are situations when SSO can introduce new risks, such as increasing the impact of compromised accounts. For example, a hacker entering a healthcare systems’ SSO with valid user credentials could potentially gain access to all applications tied to that user login.
What is multi-factor authentication?
Multi-factor authentication (MFA) enhances security by requiring users to provide multiple forms of identification to access an application.
With MFA, users typically provide two or more authentication factors, such as a password and a one-time verification code that changes. This approach significantly reduces the risk of unauthorized access to systems, even if a password is compromised.
Security experts separate MFA factors into three main categories:
1. Something you know: Factors that a user knows can include:
- passwords
- security questions
- personal identification numbers (PINs)
Tip: It’s best not to write down passwords and other things you need to access personal or company devices and tools. A small, but significant, number of security incidents can be attributed to co-workers who know where your password sticky note is. A better option? Use a password locker/manager.
2. Something you have: This authentication type involves a device or object, like a smartphone, to verify a user, such as security badges and tokens, and verification apps. For example, a user might need to enter a code they receive as a text message following their password.
The use of Proximity Authentication technology in particular is a growing trend in healthcare environments. This type of authentication technology is passwordless as it incorporates a badge to quickly log a person in or out of applications and devices.
Integrating Proximity Authentication with multi-factor authentication can offer healthcare providers a faster, more productive approach to facilitating patient care, while also ensuring proper security.
3. Something you are: This authentication method is used most often as part of high-level security requirements. They include verifications like fingerprints, facial recognition, voice recognition, and even retina scans.
Implementing multi-factor authentication
When implementing MFA, organizations choose two or more authentication factors, for example, a password and a verification code,
Your IT team can require MFA with every login (a zero trust model), or only when user’s login from a new device or an unknown network. Users simply need to verify their identity and they can safely access the applications.
To minimize the perceived inconvenience for employees, it is crucial to choose authentication factors that are user-friendly. Alternatively, you could enhance the security measures with productivity and usability benefits, such as those provided by single sign-on.
By incorporating SSO, you can add an extra layer of security while also making the authentication process more efficient and streamlined for employees.
Managing multi-factor authentication
A common vulnerability that penetration testers come across is incomplete implementation of multi-factor authentication. In some cases, this is due to certain platforms being incompatible with your MFA platform.
If/when this happens, access to these outlier systems should be strictly limited to authorized staff with a legitimate need, and only when they are connecting from trusted networks or through a VPN that supports MFA.
When it comes to using multi-factor authentication, the key to success lies in ensuring that it’s deployed intentionally and completely throughout the organization, and that employees receive sufficient training to help them understand the risks.
Any organization deploying MFA should consider these two questions:
- Where is your organization most exposed? Systems that are public-facing or external pose the most risk. Attacks against these systems and services can originate from anywhere, including nation-states, cyber terrorists, hacktivists, script kiddies, and others.
- How can organizations limit access? Not every system should be available to every employee or vendor, and most systems should never be accessed by the public. Access to IT systems should be limited to the people, departments, or job roles that legitimately need access. Everyone else should be restricted.
Weak links in the authentication chain
Regardless of the user authentication protocols within your healthcare organization, it’s imperative that technology be coupled with effective and continual user training.
More than 80% of breaches involve a human in some way. Whether it’s an inadvertent click on a malicious link in an email, or making a simple error, human missteps expose your organization to security breaches.
A somber fact is that many phishing and authentication bypass methods are designed to prey on unwary humans, and social engineering tactics tend to be especially effective among healthcare workers.
In addition to facing unique work pressures that can be distracting and stressful, healthcare workers generally are compassionate, caring, and willing to help someone in need.
Consistent training on cyber threats, enforcing complex and frequently changed passwords, and using MFA responsibly can go a long way toward minimizing the risk of an attack.
Here are a few cyber-attack tactics to consider educating your staff on:
Push notification abuse
This MFA method relies on sending push notifications to a user’s mobile phone; the user must accept a connection for an attacker to gain access.
A variation combines push notification abuse with a call or text message to victims, for example: “We don’t know each other, but I just started a new job at a company that uses the same MFA technology, and IT entered your phone number instead of mine. If you’d just accept the request, I’ll log in and change the phone number.”
These types of notifications should be a stop-and-think moment for users before hitting “accept.” Since this method can target multiple people within an organization, employees should be trained to identify and report this type of malicious activity to the IT team to help stop the attack before more employees fall victim.
Impersonating a company executive
In this situation, a threat actor pretends to be a high-ranking leader within the organization to intimidate a more junior or inexperienced employee into giving them access.
For example, an inexperienced help desk employee who receives a call from a high-ranking hospital official saying they’ve been locked out of their account. The employee asks for identification, but the “official” threatens to call the employee’s boss and report them if the account isn’t unlocked immediately.
SSO or MFA: Which is better for healthcare cybersecurity?
Single sign-on and multi-factor authentication aren’t mutually exclusive. Even though these authentication methods serve different purposes, they are complementary.
The convenience of SSO combined with the easy-to-use, hard-to-bypass MFA has led to this combo becoming the minimum authentication criteria for most public-facing applications within healthcare organizations.
These protective layers help to distance hackers from your applications, give authorized users a streamlined experience, and provide your IT staff with a powerful mechanism to monitor and control access.
To learn more about strategies and tactics for improving the security posture of your healthcare organization, check out our healthcare cybersecurity webinars.


